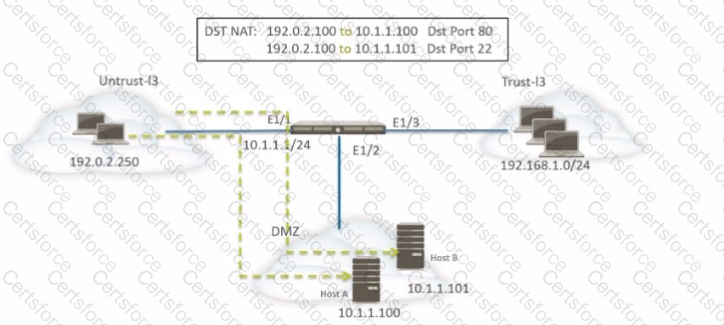
In aZero Trust Architecture (ZTA), network segmentation is critical toprevent unauthorized lateral movementwithin a flat network. Since the hospital system allowsmobile medical imaging trailersto connect directly to its internal network, this poses asignificant security risk, as these trailers may introducemalware, vulnerabilities, or unauthorized accessto sensitive medical data.
The mostcost-effectiveandpracticalsolution in this scenario is:
Creating separate security zonesfor the imaging trailers.
Applying access control and inspection policiesvia the hospital’sexisting core firewallsinstead of deploying new hardware.
Implementing strict policy enforcementto ensure that only authorized communication occurs between the trailers and the hospital’s network.
Network Segmentation for Zero Trust
By placing the medical imaging trailers in theirown firewall-enforced zone, they areisolated from the main hospital network.
Thisreduces attack surfaceand prevents an infected trailer from spreading malware to critical hospital systems.
Granular security policies ensureonly necessary communicationsoccur between zones.
Cost-Effective Approach
Usesexisting core firewallsinstead of deploying costly additional edge firewalls at every campus.
Reduces complexityby leveraging the current security infrastructure.
Visibility & Security Enforcement
Thefirewall enforces security policies, such asallowing only medical imaging protocolswhile blocking unauthorized traffic.
Integration withThreat Prevention and WildFireensures that malicious files or traffic anomalies are detected.
Logging and monitoring via Panoramahelps the security team track and respond to threats effectively.
(A) Deploy edge firewalls at each campus entry point
This is an expensive approach, requiring multiple hardware firewalls at every hospital location.
While effective, it isnot the most cost-efficientsolution when existingcore firewallscan enforce the necessary segmentation and policies.
(B) Manually inspect large images like holograms and MRIs
Thisdoes not align with Zero Trust principles.
Manual inspection is impractical, as it slows down medical workflows.
Threats do not depend on image size; malware can be embedded in small and large files alike.
(D) Configure access control lists (ACLs) on core switches
ACLs are limited in security enforcement, as they operate atLayer 3/4and do not providedeep inspection(e.g., malware scanning, user authentication, or Zero Trust enforcement).
Firewalls offerapplication-layer visibility, which ACLs on switches cannot provide.
Switches do not log and analyze threatslike firewalls do.
Firewall Deployment– Firewall-enforced network segmentation is akey practice in Zero Trust.
Security Policies–Granular policiesensure medical imaging traffic is controlled and monitored.
VPN Configurations– If remote trailers are involved, secure VPN access can be enforced within the zones.
Threat Prevention & WildFire– Firewalls can scan imaging files (e.g., DICOM images) for malware.
Panorama– Centralized visibility into all traffic between hospital zones and trailers.
Zero Trust Architectures– This solutionfollows Zero Trust principlesby segmenting untrusted devices and enforcing least privilege access.
Why Separate Zones with Enforcement is the Best Solution?Other Answer Choices AnalysisReferences and Justification:Thus,Configuring separate zones (C) is the correct answer, as it providescost-effective segmentation, Zero Trust enforcement, and security visibilityusing existing firewall infrastructure.