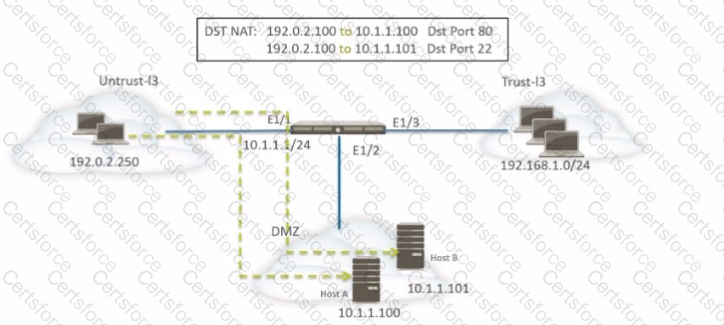
A network administrator is using DNAT to map two servers to one public IP address. Traffic will be directed to a specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.
Which two sets of Security policy rules will accomplish this configuration? (Choose two.)
Submit