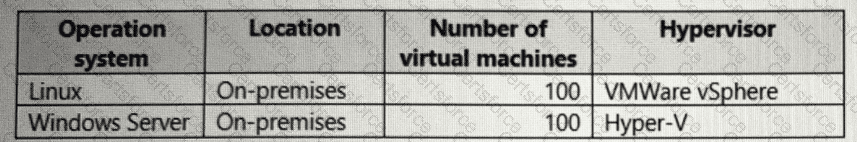
Your company has the virtual machine infrastructure shown in the following table.
The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure.
You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware.
What should you include in the recommendation?
Your company uses Microsoft Defender for Cloud and Microsoft Sentinel. The company is designing an application that will have the architecture shown in the following exhibit.
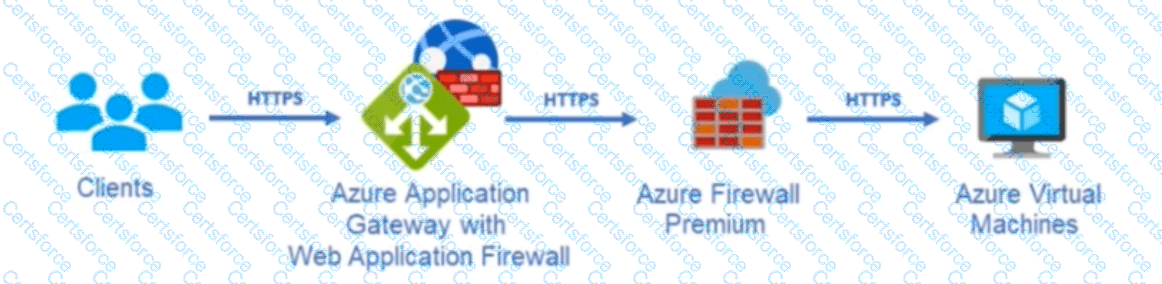
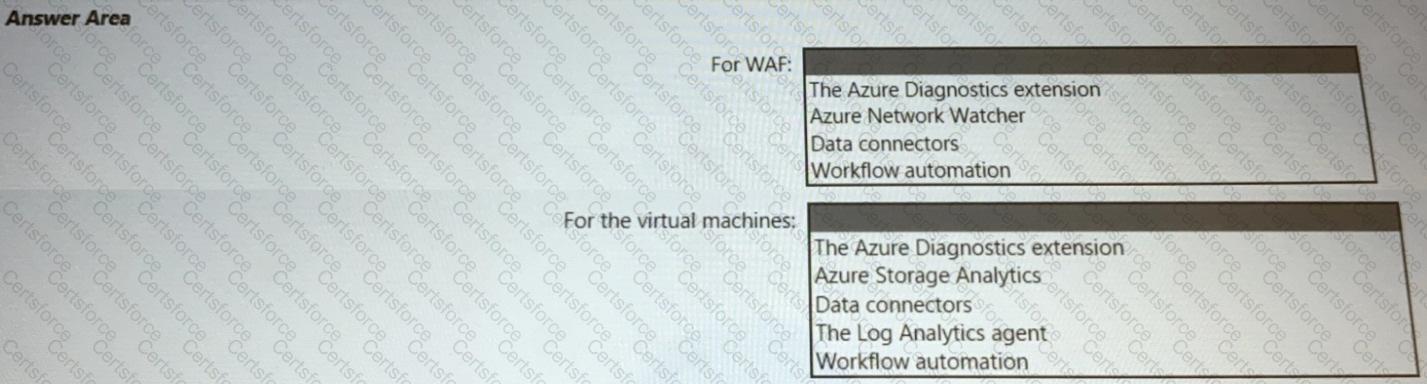
You are designing a logging and auditing solution for the proposed architecture. The solution must meet the following requirements-.
• Integrate Azure Web Application Firewall (WAF) logs with Microsoft Sentinel.
• Use Defender for Cloud to review alerts from the virtual machines.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 stores documents that are based on a predefined form and include confidential employee information.
You monitor access to Site1 by using a Microsoft Defender for Cloud Apps session policy.
You need to ensure that step-up authentication is triggered when a user downloads documents that are based on the predefined form. The solution must minimize administrative effort.
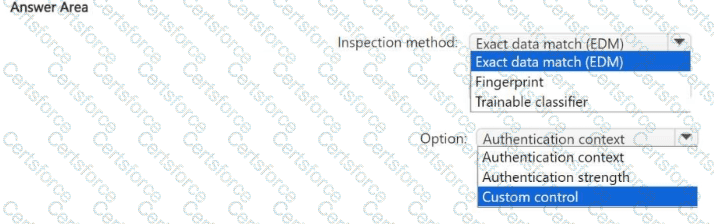
Which Microsoft Data Classification Service inspection method should you use, and which Conditional Access option should you add to the session policy? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that is used as an Azure landing zone for an application. You need to evaluate the security posture of all the workloads in the landing zone. What should you do first?
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation.
You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc. Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
You have three Microsoft Entra tenants named Tenant 1. Tenant2. and Tenant3.
You have three Azure subscriptions named Sub1, Sub2, and Sub3. Each tenant is associated with multiple Azure subscriptions.
Each subscription contains a single Microsoft Sentinel workspace as shown in the following table.
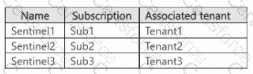
You need to recommend a solution that meets the following requirements:
• Ensures that the users in Tenant1 can manage the resources in Sub2 and Sub3 without having to switch subscriptions or sign in to a different tenant
• Implements multiple workspace view for Sentinel2 and Sentinel3
What should you use to delegate permissions, and which Microsoft Sentinel feature will users be able to manage in multiple workspace view? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
You are planning the security levels for a security access strategy.
You need to identify which job roles to configure at which security levels. The solution must meet security best practices of the Microsoft Cybersecurity Reference Architectures (MCRA).
Which security level should you configure for each job role? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
