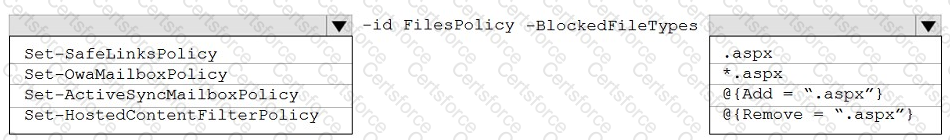
You need to modify FilesPolicy to prevent users from downloading ASPX files. The solution must meet the technical requirements.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
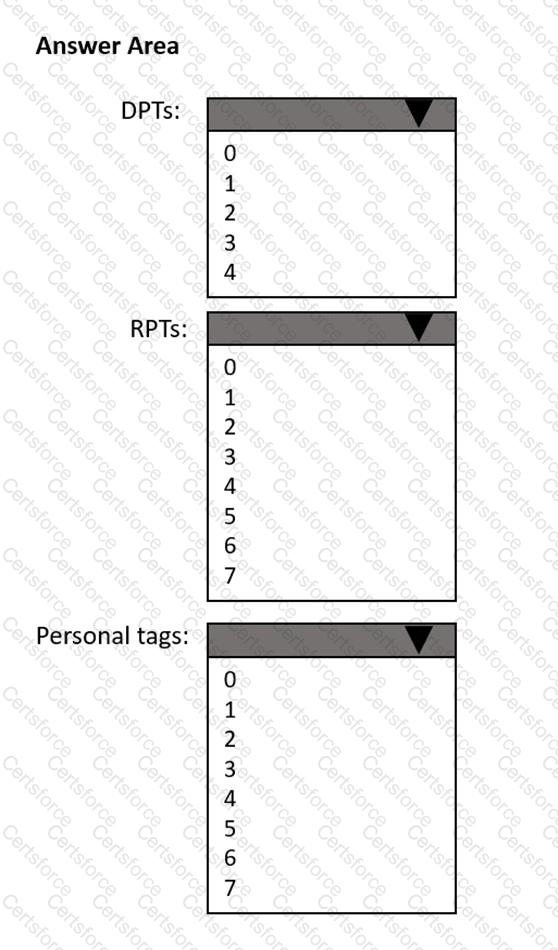
How many default policy tags (DPTs), retention policy tags (RPTs), and personal tags should you create to meet the retention requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
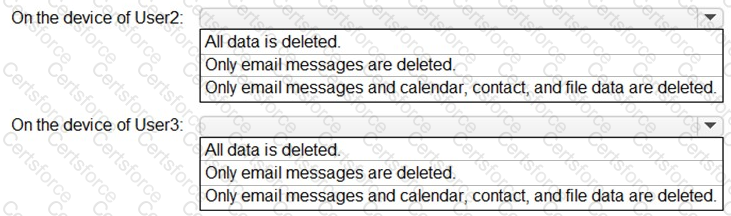
You need to perform a remote wipe of the devices of User2 and User3.
You run the following commands.
Clear-MobileDevice -id User2-Device
-NotificationEmailAddress "admin@Fabrikam.com"
Clear-MobileDevice -id User3-Device
-NotificationEmailAddress "admin@Fabrikam.com"
What occurs on each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to generate a report for the mobile devices that meets the technical requirements.
Which PowerShell cmdlet should you use?
You need to encrypt email between Fabrikam and Litware to support the planned changes.
What should you configure in the Exchange admin center?
You need to identify which users clicked the links in the phishing emails.
What should you do?
User3 leaves the company.
You need to ensure that Admin1 and Admin2 can access the mailbox of User3. The solution must meet the technical requirements.
What should you do?
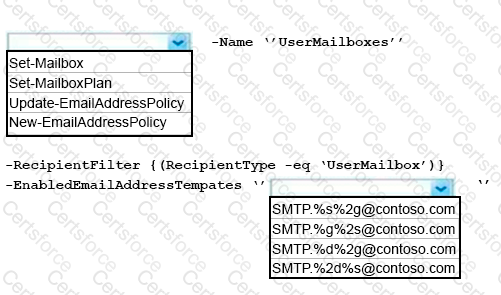
You need to configure the environment to support the planned changes for email addresses.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution that meets the security requirements for protecting users.
What should you recommend?
You must prevent HelpDeskUser1 from repeating the same mistake.
You need to identify which management role provided HelpDeskUser1 with the necessary permissions to make the mistake identified in the problem statement.
Which two cmdlets should you run? Each correct answer presents part of the solution.