Which monitoring solution should you configure to meet the security requirements?
Which two actions should you perform to meet the security requirements for Defender for Endpoint? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What should you do to meet the application requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
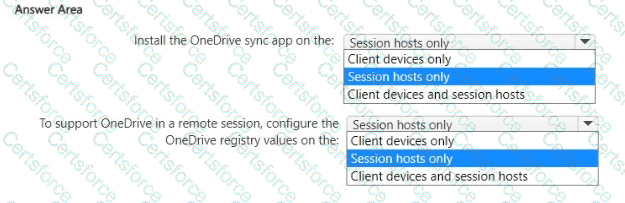
What should you do to meet the user profile requirements?
What should you do to ensure that the session hosts meet the application requirements for App1?
What should you configure to meet the networking requirements?
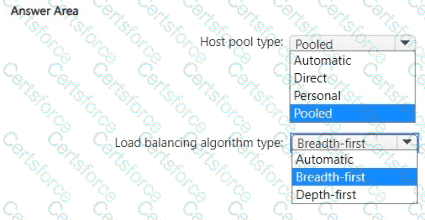
Which type of host pool and load balancing algorithm should you configure to meet the performance requirements? To answer, select the appropriate options in The answer area.
NOTE: Each correct selection is worth one point.
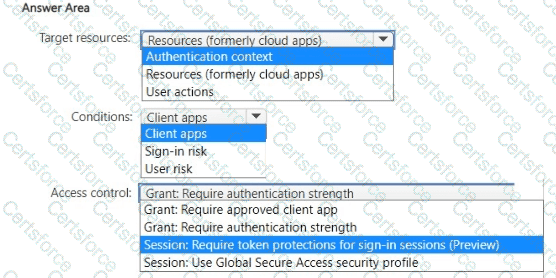
You need to create a Conditional Access policy to meet the security require-ments.
How should you configure the policy? To answer, select the appropriate options in the answer area.
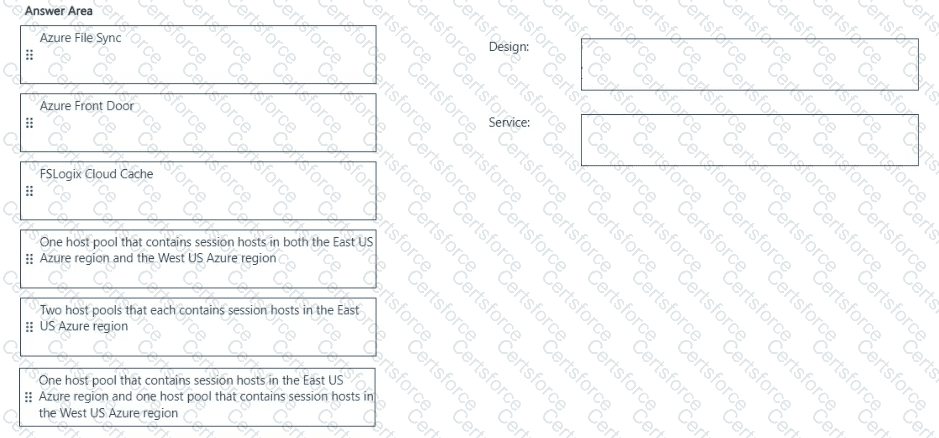
Which host pool design and which service should you configure to meet the disaster recovery requirements? To answer, drag the appropriate solution to the correct requirements. Each solution may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content
NOTE: Each correct selection is worth one point.
You need to prepare the disk on VM1 for use with the Azure Virtual Desktop deployment. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.