Which two statements about the host-inbound-traffic parameter in a zone configuration are correct? (Choose two.)
You are troubleshooting traffic traversing the SRX Series Firewall and require detailed information showing how the flow module is handling the traffic.
How would you accomplish this task?
Which security policy action will cause traffic to drop and a message to be sent to the source?
You want to enable NextGen Web Filtering in SRX Series devices.
In this scenario, which two actions will accomplish this task? (Choose two.)
What happens if no match is found in both zone-based and global security policies?
Which two statements about global security policies are correct? (Choose two.)
You have created a series of security policies permitting access to a variety of services. You now want to create a policy that blocks access to all other services for all user groups.
What should you create in this scenario?
Which two statements are correct about unified security policies? (Choose two.)
You are troubleshooting first path traffic not passing through an SRX Series Firewall. You have determined that the traffic is ingressing and egressing the correct interfaces using a route lookup.
In this scenario, what is the next step in troubleshooting why the device may be dropping the traffic?
Click the Exhibit button.
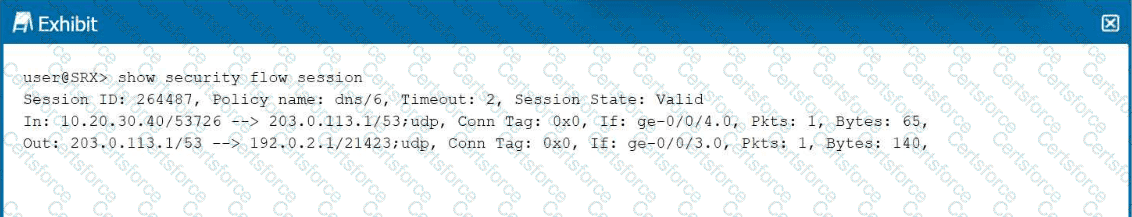
Referring to the exhibit, which two statements are correct about the traffic flow shown in the exhibit? (Choose two.)