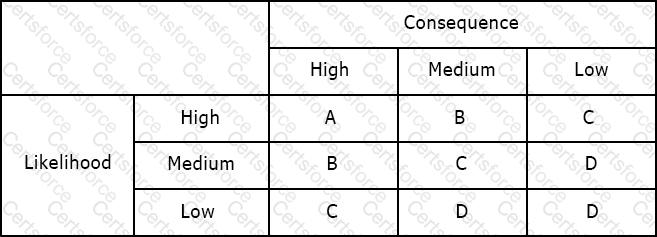
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
A plant has several zones including business, safety-critical, and wireless zones. According to ISA/IEC 62443, how should these zones be managed during risk assessment?
Which of the following is NOT a general class of firewalls?
Which is the implementation of PROFIBUS over Ethernet for non-safety-related communications?
Available Choices (select all choices that are correct)
Which of the following is an example of a device used for intrusion detection?
What type of security level defines what a component or system is capable of meeting?
Available Choices (select all choices that are correct)
What.are the two elements of the risk analysis category of an IACS?
Available Choices (select all choices that are correct)
Which of the following BEST describes ‘Vulnerability’?
What programs are MOST effective if they are tailored to the audience, consistent with company policy, and communicated regularly?
How does ISA/IEC 62443-2-1 suggest integrating the IACS Security Program (SP) within an organization?