Which of the following options will not pose a security threat to the network?
In the terminal security management, the black and white list mode is used to check the terminal host software installation status. Which of the following situations is a compliant behavior?
What are the typical technologies of anti-virus engines (multiple choice)
Which of the following technologies can achieve content security? (multiple choice)
Which of the following options are relevant to Any Office The description of the solution content is correct? (Multiple choice)
Regarding Huawei's anti-virus technology, which of the following statements is wrong?
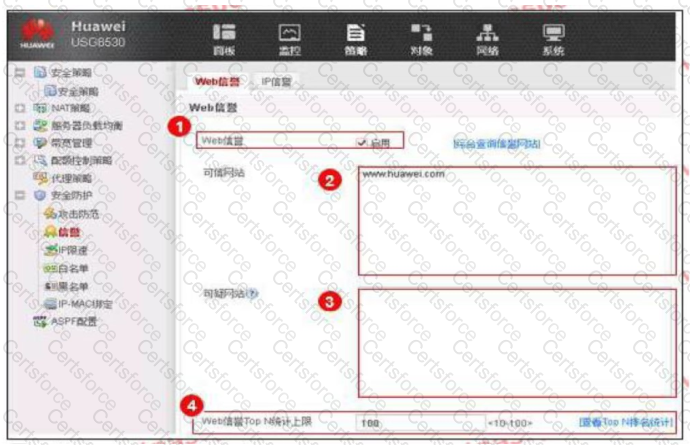
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
Viruses can damage computer systems. v Change and damage business data: spyware collects, uses, and disperses sensitive information of corporate employees.
These malicious pastoral software seriously disturb the normal business of the enterprise. Desktop anti-disease software can solve the problem of central virus and indirect software from the overall situation.
Due to differences in network environment and system security strategies, intrusion detection systems are also different in specific implementation. From the perspective of system composition, the main
Which four major components are included?
Regarding MAC authentication and MAC bypass authentication, which of the following descriptions are correct? (multiple choice)