Which of the following signature attributes cannot be configured for IP custom signature?
Attacks on the Web can be divided into three types of attacks on the client, server, or communication channel.
IPS is an intelligent intrusion detection and defense product. It can not only detect the occurrence of intrusions, but also can respond in real time through certain response methods.
Stop the occurrence and development of intrusions, and protect the information system from substantial attacks in real time. According to the description of PS, the following items are wrong?
Which of the following threats cannot be detected by IPS?
In the penetration stage of an APT attack, which of the following attack behaviors will the attacker generally have?
Which of the following files can the sandbox detect? (multiple choice)
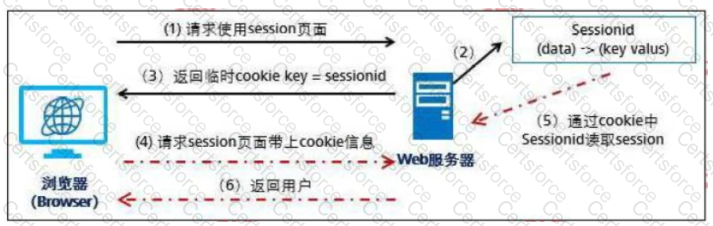
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
The status code in the HTTP response message indicates the type of the response message, and there are many possible values. Which of the following status codes represents the client request
The resource does not exist?
Which of the following behaviors is a false positive of the intrusion detection system?
Which of the following options is not a defense against HTTP Flood attacks?