Regarding the characteristics of the routing table, which of the following items is described correctly
As shown in the figure, nat server global202.106.1.1 inside10.10.1.1 is configured on the firewall. Which of the following is the correct configuration for interzone rules? ( )[Multiple choice]*

Please match the following information security risks to information security incidents one by one.[fill in the blank]*
physical security riskEnterprise server permissions are loosely set
Information Security Management RiskInfected Panda Burning Incense
Information Access RiskFire destroyed equipment in computer room
application riskTalk to people about leaking company secrets
Which of the following characteristics does a denial-of-service attack include?
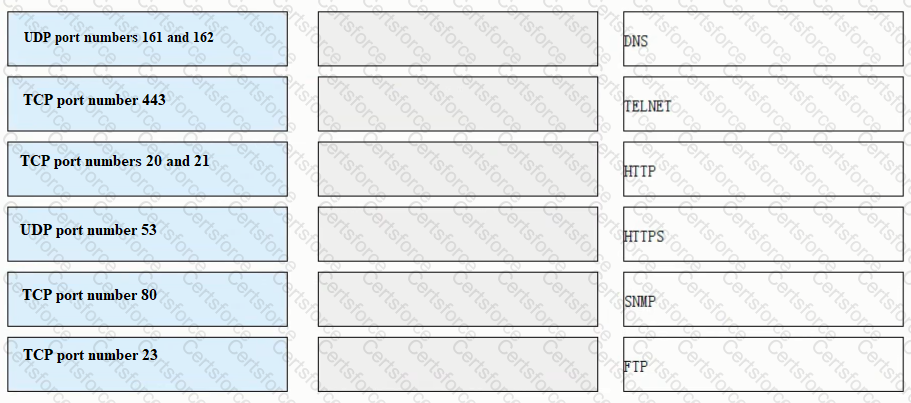
Match each of the following application layer service protocols with the correct transport layer protocols and port numbers.
Please classify the following security defenses into the correct classification.

Using the ___ method of the Web proxy, the virtual gateway will encrypt the real URL that the user wants to access, and can adapt to different terminal types.[fill in the blank]*
Please order the following steps in the PKI life cycle correctly, 1. Issued, 2. storage, 3. Update, 4. verify[fill in the blank]*
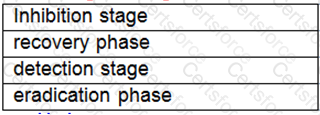
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*
When using passive mode to establish an FTP connection, the control channel uses port 20 and the data channel uses port 21. ( )[Multiple choice]*