Which directory in JAR files is used to store package and extension configuration data?
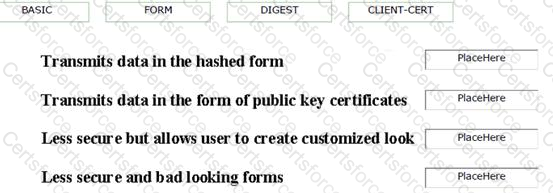
Drag and drop the appropriate authentication types from the given options to match their properties.
Which of the following methods is used to authenticate the users, and if the user has not been authenticated, the method returns false?
Which of the following functions are performed by methods of the
HttpSessionActivationListener interface?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following listeners causes an object of the implementing class to be notified when it is added to or removed from a session?
Mark works as a Programmer for InfoTech Inc. He develops a Java application that uses the encryption and compression techniques. Which of the following interfaces will he use to control the serialization and deserialization processes?
Which of the following fields must be present in the login page when using the form-based
authentication?
Each correct answer represents a part of the solution. Choose two.
Which of the following is a mandatory sub-element of the
You work as a Software Developer for UcTech Inc. You create a session using the HttpSession interface. You want the attributes to be informed when the session is moved from one JVM to another and also when an attribute is added or removed from the session. Which of the following interfaces can you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Programmer for Technostar Inc. He writes the following code using Java.
1. class WrapperClass{
2. public static void main(String[] argv){
3. String str2 = Double.toString(12);
4. String str1 = Double.toHexString(12);
5. System.out.println(str1+str2);
6. }
7. }
What will happen when John attempts to compile and execute the code?