During a password guessing attack, which HTTP request method would a Python program most commonly call to submit a usemame and password to a target website?
An attacker does not yet know the IP address of his target. He uses the "socket" module to create a backdoor program. He is writing the command to bind the computer's current IP address and port 4444 to the "backdoor" socket. Which command should he use?
A log file is stored in variable "a". The file has the following format for each log entry, in order, stored in big endian:
Field 1: 2-byte integer
Field 2: 2-byte integer
Field 3: 4-byte string
Which of the following would unpack a line from the log file into the proper fields?
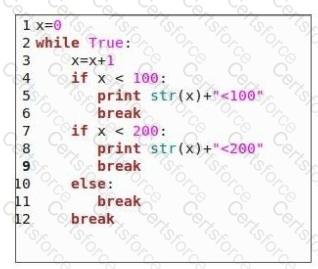
How many lines will the following code print?
What does the attacker do in a SQL Injection attack?
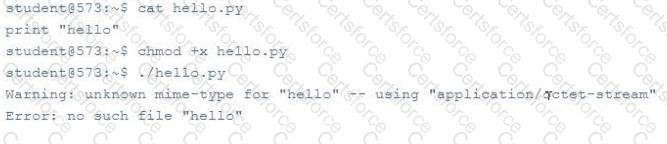
A programmer attempts to run the Python program hello.py as follows, but an error occurs. What is the cause of this error?
Which of the following will be the value of the variable y?

What does the following command do?
pip search syslog
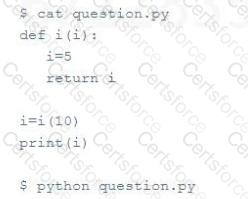
When the following program "question.py" is executed with Python what is the output?
When using the Python "sockets" module, which of the following calls is used to transmit data to a specific IP address?