Microsoft.Key Vault is an example of which component of Azure's structure?
A company is creating an incident response team that will be part of their existing GCP Organization. Where in the organizational structure should their services be placed?
Communication between the VPN client and Azure VNet1via VPN Tunnel #1 is using which of the following connections?
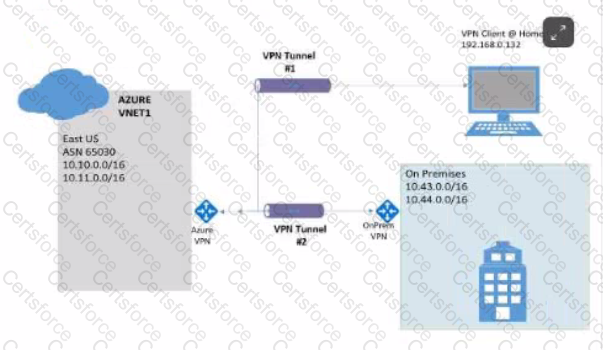
What is the recommended storage type when creating an initial snapshot of a VM in Azure for forensic analysis?
What is the maximum file size for Azure Page Blob storage?
Which statement describes a zld.metal EC2 instance?
An investigator his successfully installed the ExchangeOnlineManagement module on their investigation system and is attempting to search a client's Microsoft 365 Unified Audit Log using PowerShell. PowerShell returns a "command not found" error each time they try to execute the Search-UnifiedAuditLog cmdlet. How should the investigator troubleshoot this issue?
Which is the effective access when aws user is assigned to an S3 bucket?
What type of AWS log is the following snippet an example of?
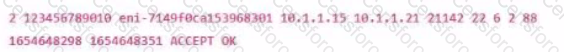
In which scenario would an investigator collect NetFlow logs rather than PCAP logs?