Acme Corporation performed an investigation of its centralized logging capabilities. It found that the central server is missing several types of logs from three servers in Acme's inventory. Given these findings, what is the most appropriate next step?
Which of the following is a benefit of stress-testing a network?
An Internet retailer's database was recently exploited by a foreign criminal organization via a remote attack. The initial exploit resulted in immediate root-level access. What could have been done to prevent this level of access being given to the intruder upon successful exploitation?
What is the first step suggested before implementing any single CIS Control?
Below is a screenshot from a deployed next-generation firewall. These configuration settings would be a defensive measure for which CIS Control?
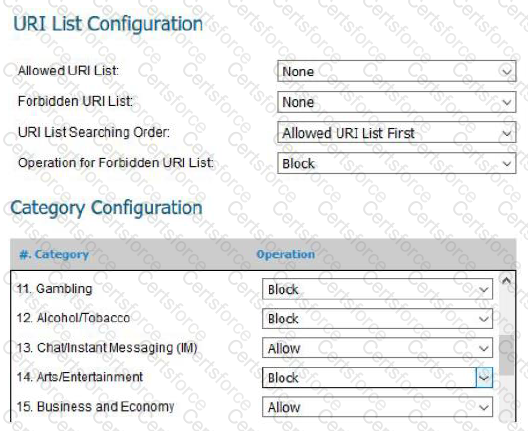
The settings in the screenshot would be configured as part of which CIS Control?
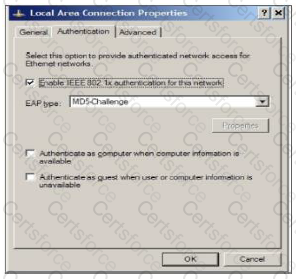
Which of the following is necessary for implementing and automating the Continuous Vulnerability Assessment and Remediation CIS Control?
Which of the following statements is appropriate in an incident response report?
Which type of scan is best able to determine if user workstations are missing any important patches?
An administrator looking at a web application’s log file found login attempts by the same host over several seconds. Each user ID was attempted with three different passwords. The event took place over 5 seconds.
ROOT
TEST
ADMIN
SQL
USER
NAGIOSGUEST
What is the most likely source of this event?