Which of the following items would be used reactively for incident response?
An organization is implementing a control for the Limitation and Control of Network Ports, Protocols, and Services CIS Control. Which action should they take when they discover that an application running on a web server is no longer needed?
An organization has implemented a policy to detect and remove malicious software from its network. Which of the following actions is focused on correcting rather than preventing attack?
According to attack lifecycle models, what is the attacker’s first step in compromising an organization?
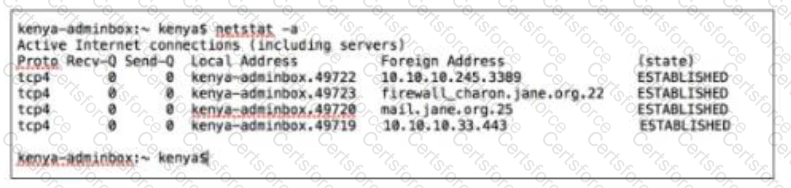
Kenya is a system administrator for SANS. Per the recommendations of the CIS Controls she has a dedicated host (kenya- adminbox / 10.10.10.10) for any administrative tasks. She logs into the dedicated host with her domain admin credentials. Which of the following connections should not exist from kenya-adminbox?
As part of a scheduled network discovery scan, what function should the automated scanning tool perform?
John a network administrator at Northeast High School. Faculty have been complaining that although they can detect and authenticate to the faculty wireless network, they are unable to connect. While troubleshooting, John discovers that the wireless network server is out of DHCP addresses due to a large number of unauthorized student devices connecting to the network. Which course of action would be an effective temporary stopgap to secure the network until a permanent solution can be found?
What is the relationship between a service and its associated port?
If an attacker wanted to dump hashes or run wmic commands on a target machine, which of the following tools would he use?
Which of the following actions will assist an organization specifically with implementing web application software security?