When examining the iOS device shown below the tool indicates that there are 4 chat messages recovered from the device.
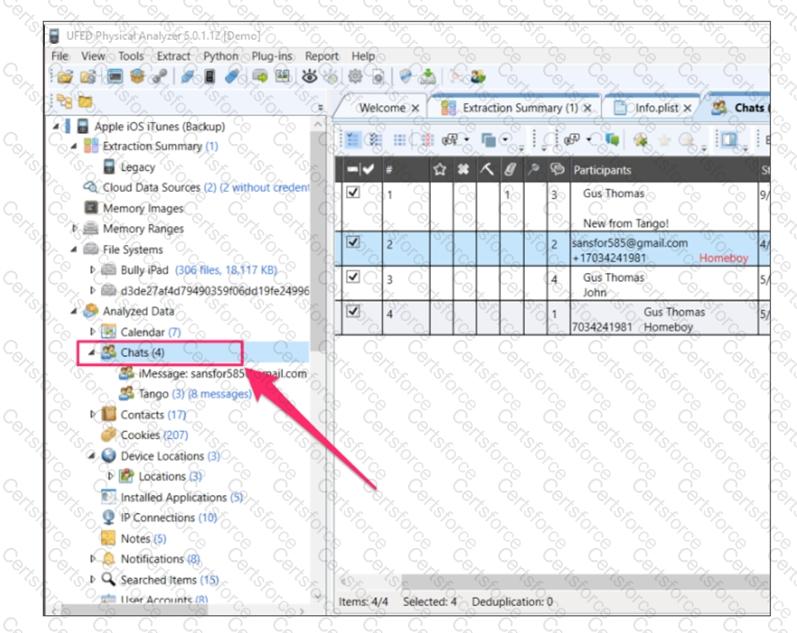
Which of the following locations may contain additional chat information?
Which of the following is a backup tool for smartphones?
Review the two highlighted sections in the hex output below from the file MP0c_000.
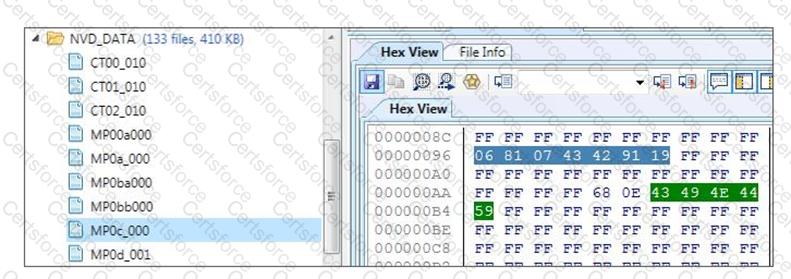
Convert the phone number found in raw format extracted from a Chinese knock-off device.
Which of the following files provides the most accurate reflection of the device’s date/timestamp related to the
last device wipe?
Which file type below is commonly associated with locational data and is an export option from within
Cellebrite Physical Analyzer and XRY to provide detailed visual output of geographic information?
Which of the following is of most concern when attempting to root an Android device such as Google Glass
when conducting a forensic acquisition?
Review the sample database.
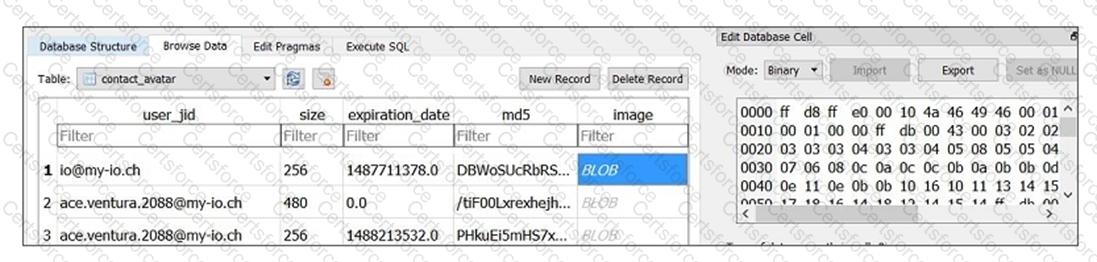
What is the BLOB column storing for this particular database table?
Property list (Plist) files are used by iOS devices to store datA. Which of the file formats below is common to
plist files?
When dealing with mobile devices and flash memory, and the fact that data in memory constantly changes
even when the device is simply powered on. It is best practice to:
Which artifact must be carved out manually when examining a file system acquisition of an Android device?