What is the MAIN difference between a Full Root and a Shell/Soft Root?
Cellebrite’s Physical Analyzer will conduct a Quick Scan for images, which goes through and carves files that may have been deleted from the device. When carving for image files, which of the following methods is most effectively used to recover data?
Which iOS backup file will contain the last time the device was backed up?
Which of the following chipsets is commonly found in knock-off handsets?
What information can you determine by reviewing the (bp2p) file from a BlackBerry OS10 handset?
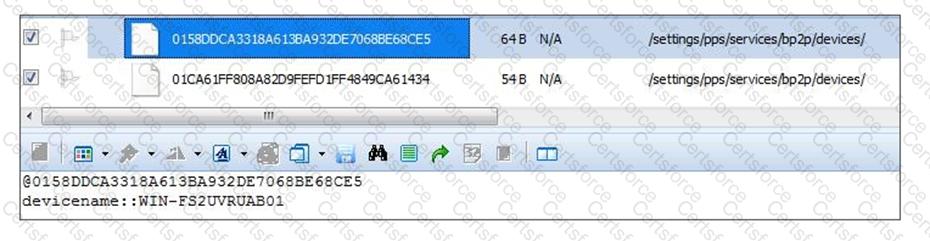
What is the essential piece of information is most often required in order to decrypt the contents of BlackBerry OS 10 handsets?
What is a risk to the security of an iPhone backup if the user selects to set a password and encrypt their
backup?
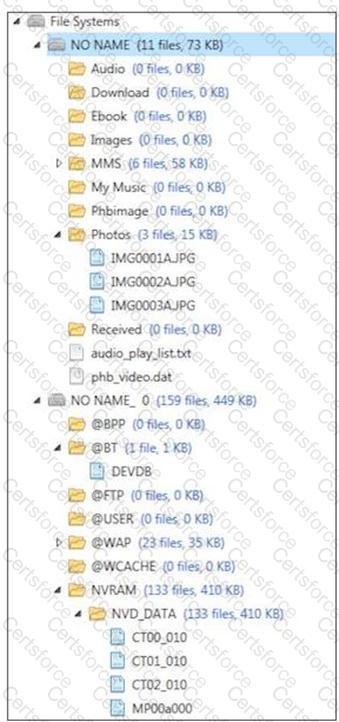
Based on the image below, which file system is being examined?
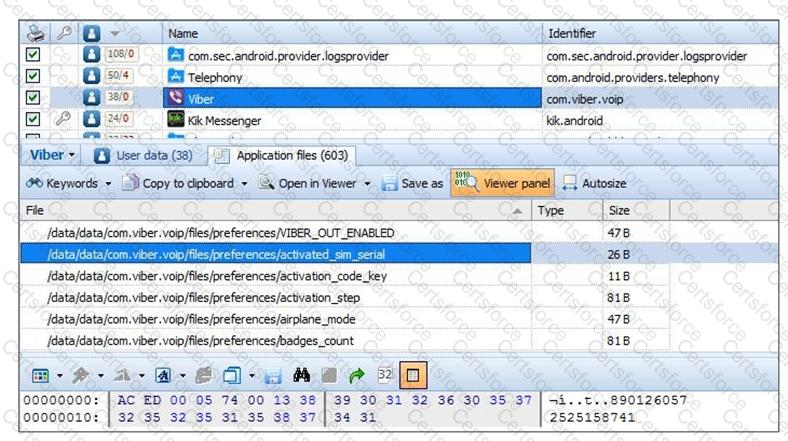
Review the information contained within the Viber application running on an Android device. Which of the
following can be determined?
Which of the following files contains details regarding the encryption state of an iTunes backup file?