Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
Refer to the exhibits.
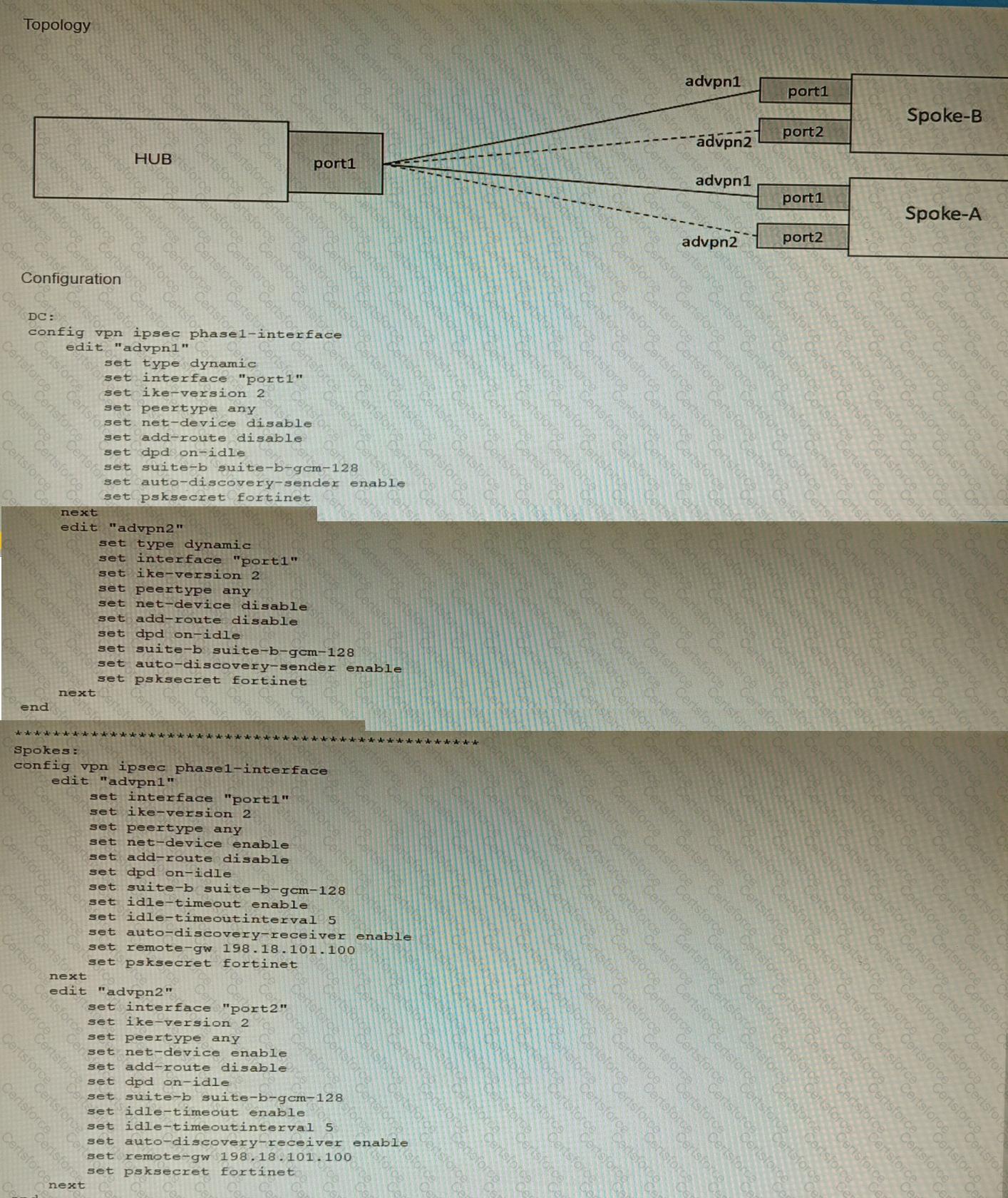
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
Refer to the exhibit.
What is happening in this scenario?
What is the benefit of using FortiGate NAC LAN Segments?
Refer to the exhibit.
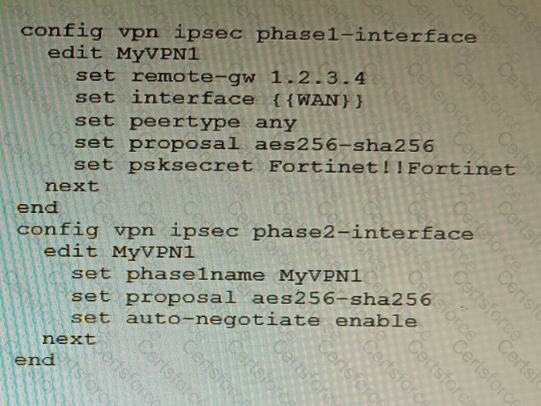
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
Refer to the exhibits.
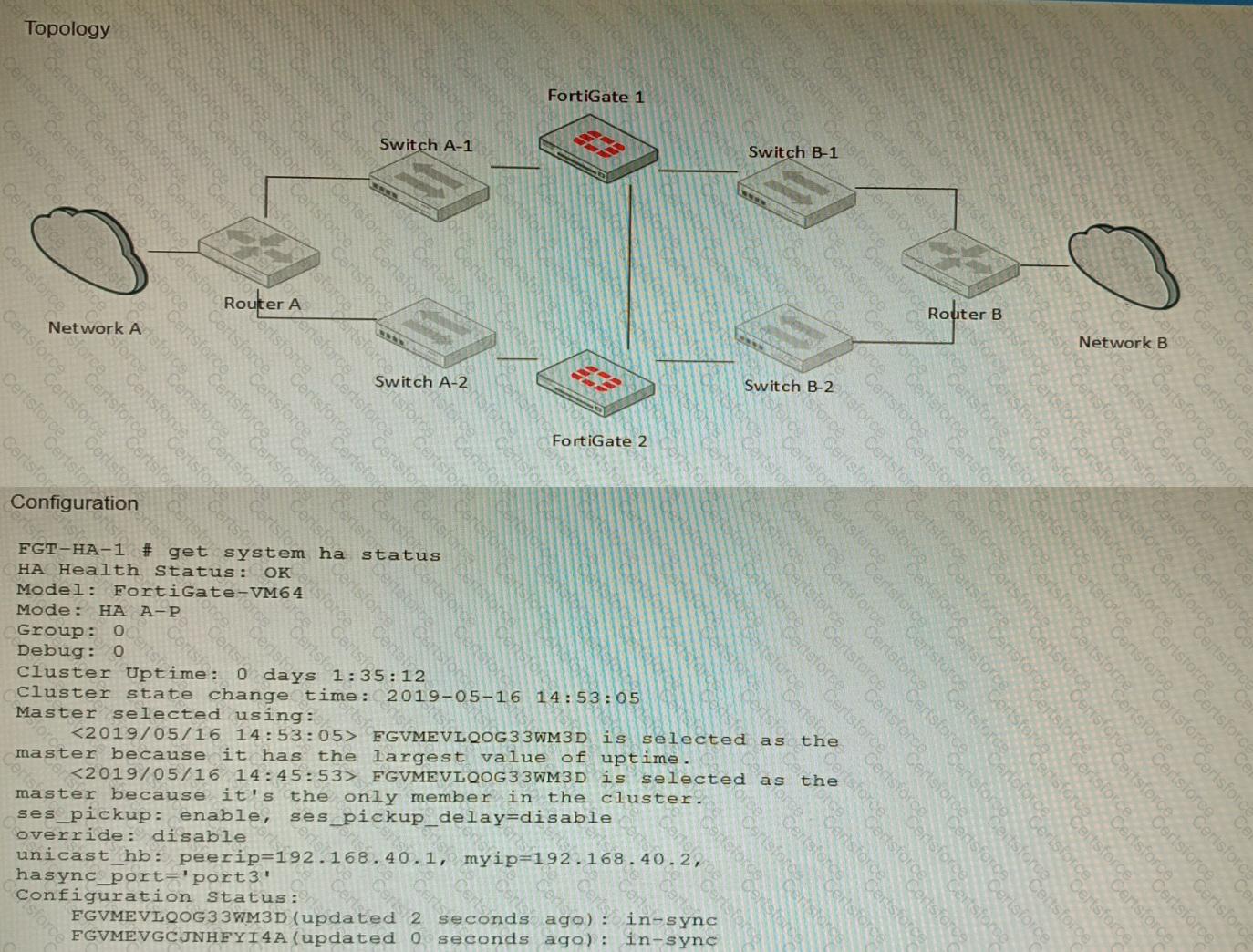
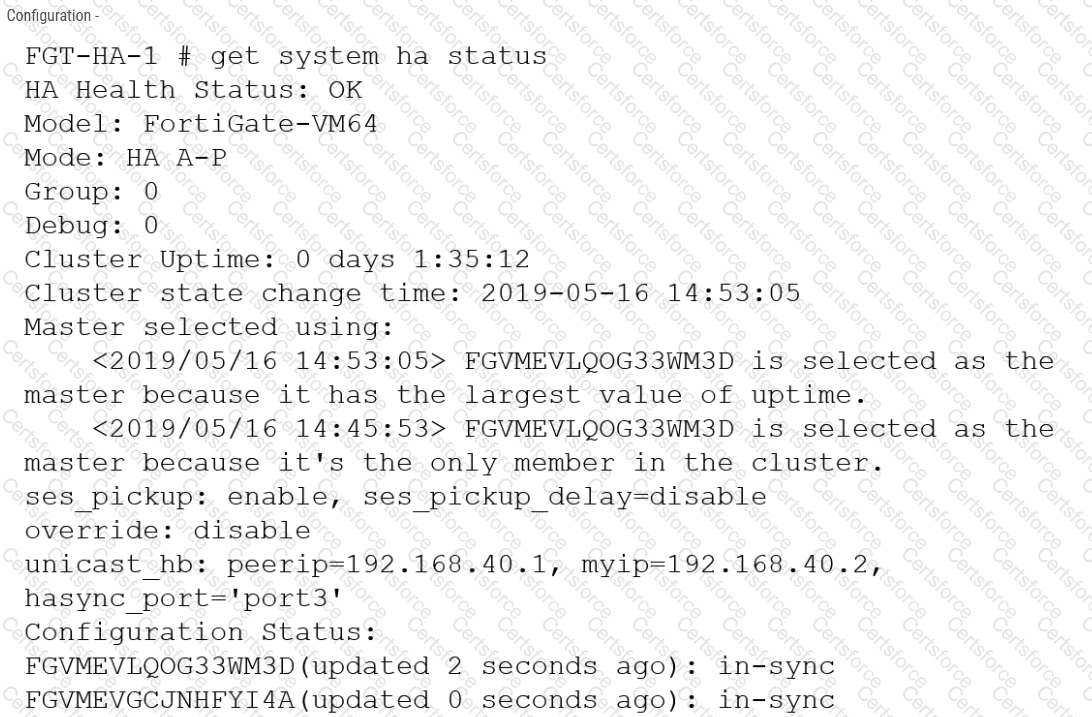
The exhibits show a FortiGate network topology and the output of the status of high availability on the FortiGate.
Given this information, which statement is correct?
An HA topology is using the following configuration:
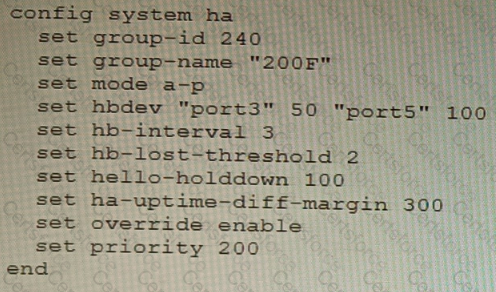
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
Refer to the CLI configuration of an SSL inspection profile from a FortiGate device configured to protect a web server:
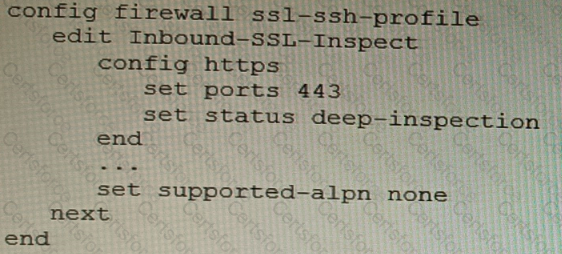
Based on the information shown, what is the expected behavior when an HTTP/2 request comes in?
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
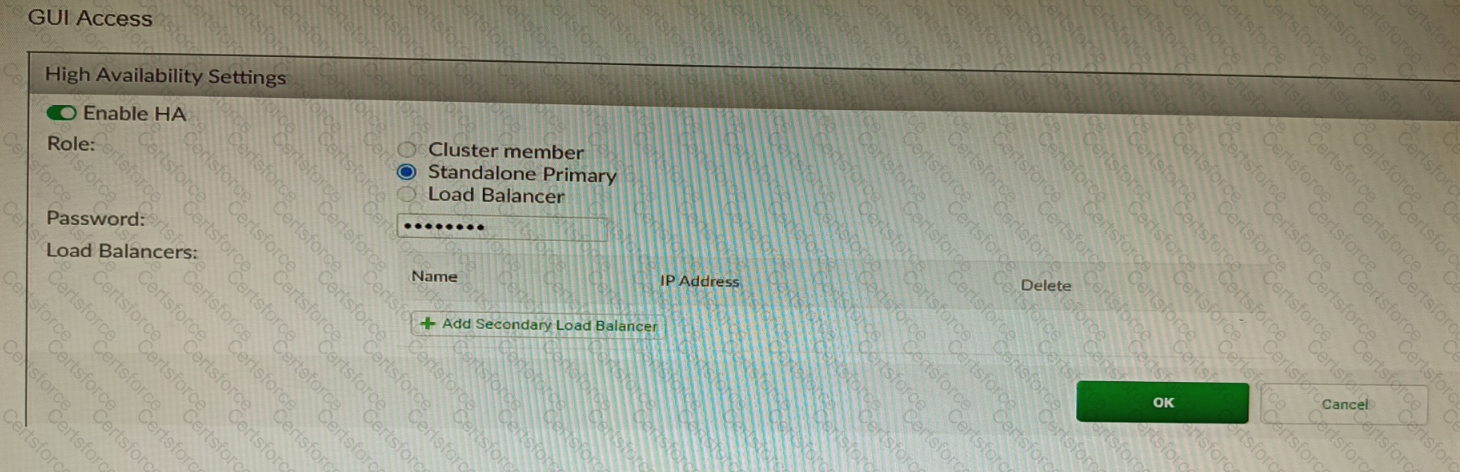
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?