The SD-WAN overlay template helps to prepare SD-WAN deployments. To complete the tasks performed by the SD-WAN overlay template, the administrator must perform some post-run tasks. What are three mandatory post-run tasks that must be performed? (Choose three.)
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
What are two reasons for using FortiManager to organize and manage the network for a group of FortiGate devices? (Choose two.)
Which are three key routing principles in SD-WAN? (Choose three.)
Which two statements about the SD-WAN zone configuration are true? (Choose two.)
Which two performance SLA protocols enable you to verify that the server response contains a specific value? (Choose two.)
Refer to the exhibit.
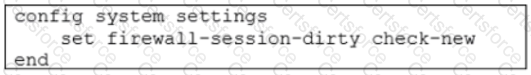
Based on the exhibit, which two actions does FortiGate perform on sessions after a firewall policy change? (Choose two.)
Refer to the exhibits.
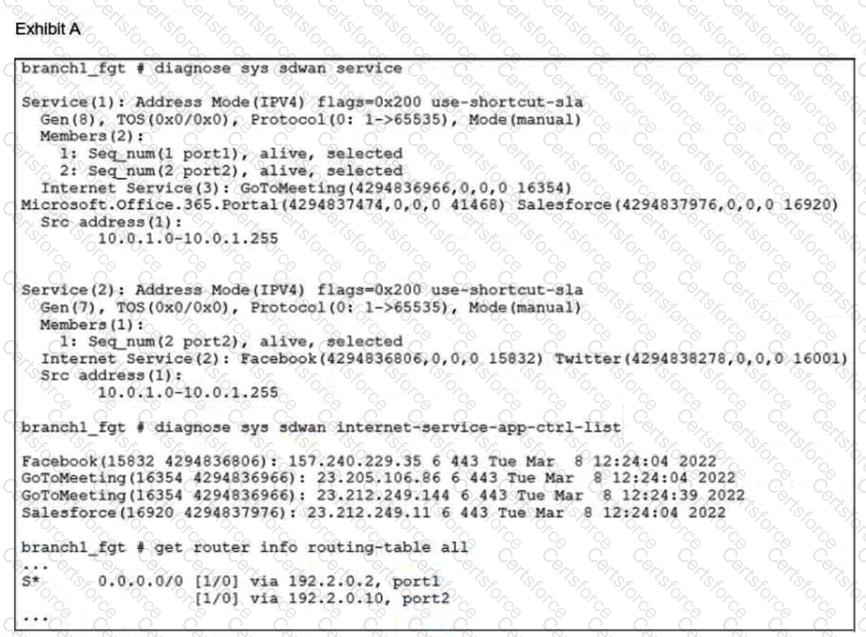
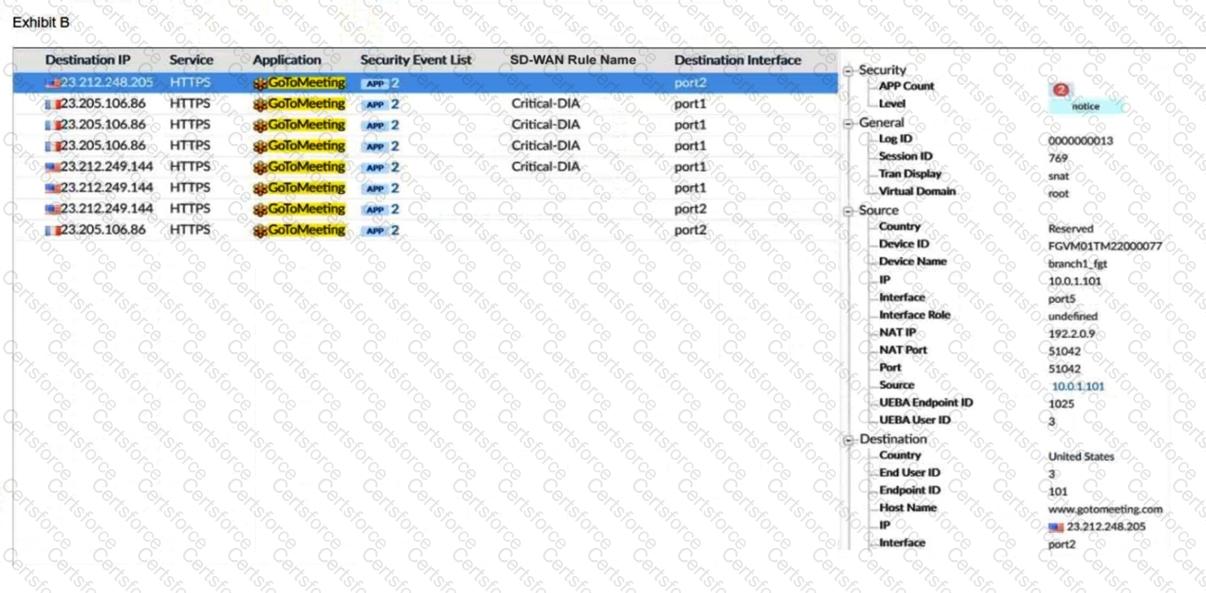
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in exhibit A.
After generating GoToMeeting test traffic, the administrator examined the respective traffic log on FortiAnalyzer, which is shown in exhibit B. The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why the traffic matched the implicit SD-WAN rule? (Choose two.)
Which two interfaces are considered overlay links? (Choose two.)