Refer to the exhibit.
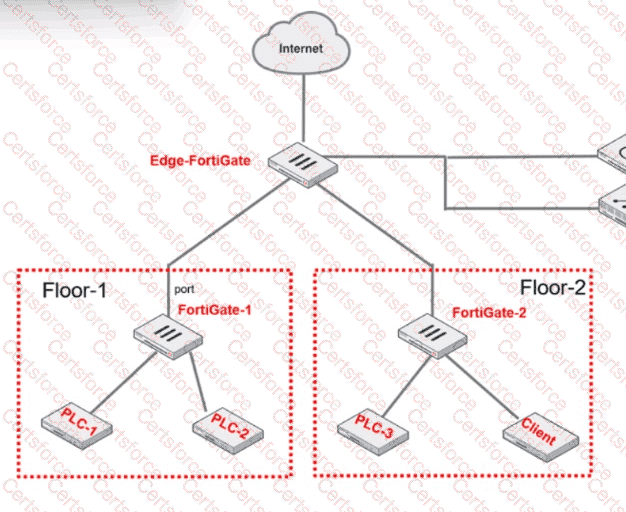
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2 level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
Refer to the exhibit, which shows a non-protected OT environment.
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
As an OT network administrator you are managing three FortiGate devices that each protect different levels on the Purdue model To increase traffic visibility you are required to implement additional security measures to detect protocols from PLCs
Which security sensor must you implement to detect protocols on the OT network?
Refer to the exhibits.
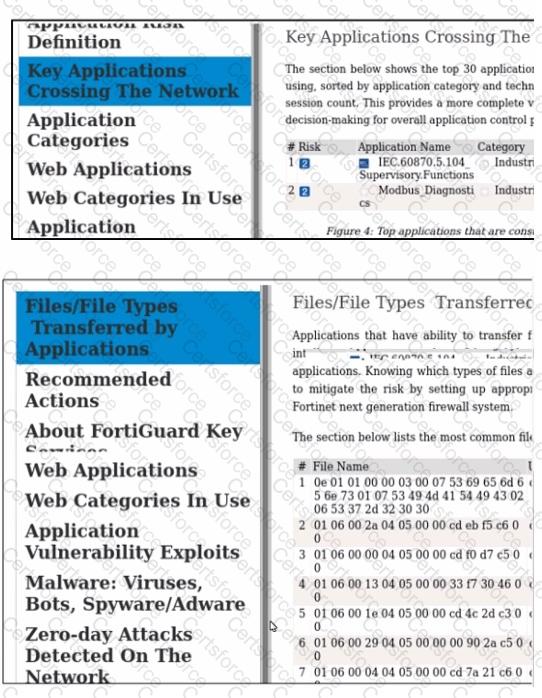
Which statement about some of the generated report elements from FortiAnalyzer is true?
Refer to the exhibit.
Given the configurations on the FortiGate, which statement is true?
An OT network architect must deploy a solution to protect fuel pumps in an industrial remote network. All the fuel pumps must be closely monitored from the corporate network for any temperature fluctuations.
How can the OT network architect achieve this goal?
Which three common breach points can be found in a typical OT environment? (Choose three.)
Refer to the exhibit.
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric? (Choose three.)
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
Which three Fortinet products can you use for device identification in an OT industrial control system (ICS)? (Choose three.)