Which three statements about SMTPS and SMTP over TLS are true? (Choose three.)
Refer to the exhibit.

MTA-1 is delivering an email intended for User 1 to MTA-2.
Which two statements about protocol usage between the devices are true? (Choose two.)
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
Refer to the exhibit.
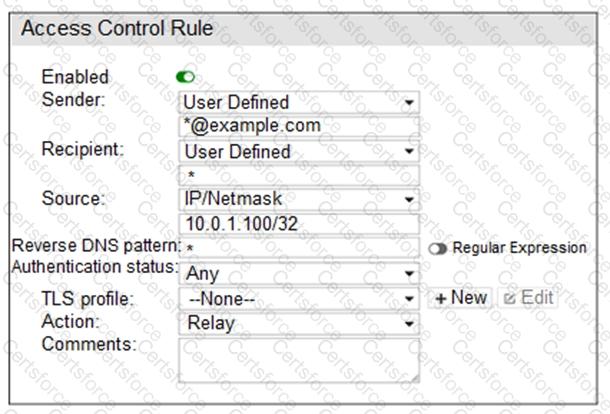
Which two statements about the access receive rule are true? (Choose two.)
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
Refer to the exhibit.
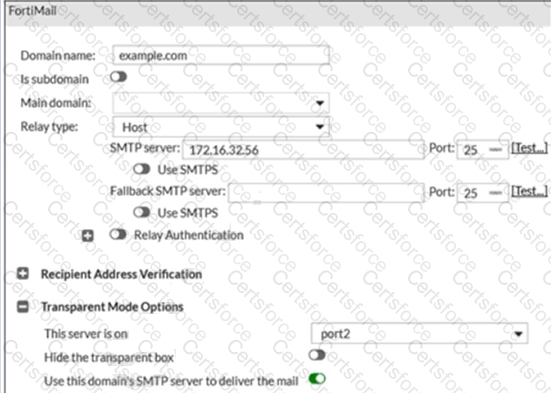
For the transparent mode FortiMail shown in the exhibit, which two sessions are considered incoming sessions? (Choose two.)