How will configuring set tcp-mss-sender and set tcp-mss-receiver in a firewall policy affect the size and handling of TCP packets in the network?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Refer to the exhibit, which shows the HA status of an active-passive cluster.
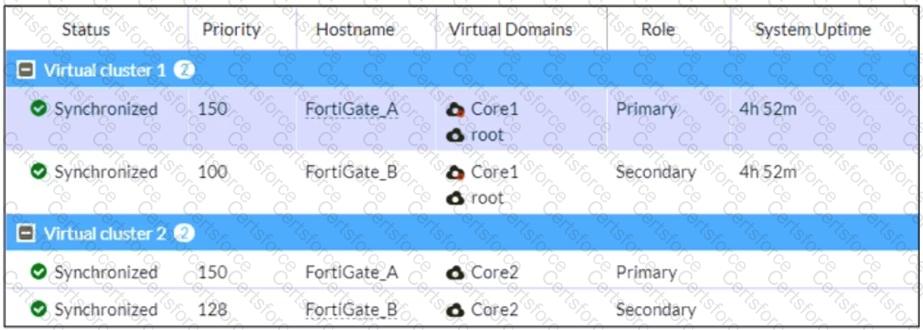
An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?
An administrator is setting up an ADVPN configuration and wants to ensure that peer IDs are not exposed during VPN establishment.
Which protocol can the administrator use to enhance security?
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
An administrator wants to scale the IBGP sessions and optimize the routing table in an IBGP network.
Which parameter should the administrator configure?
Refer to the exhibit, which shows the ADVPN IPsec interface representing the VPN IPsec phase 1 from Hub A to Spoke 1 and Spoke 2, and from Hub В to Spoke 3 and Spoke 4.
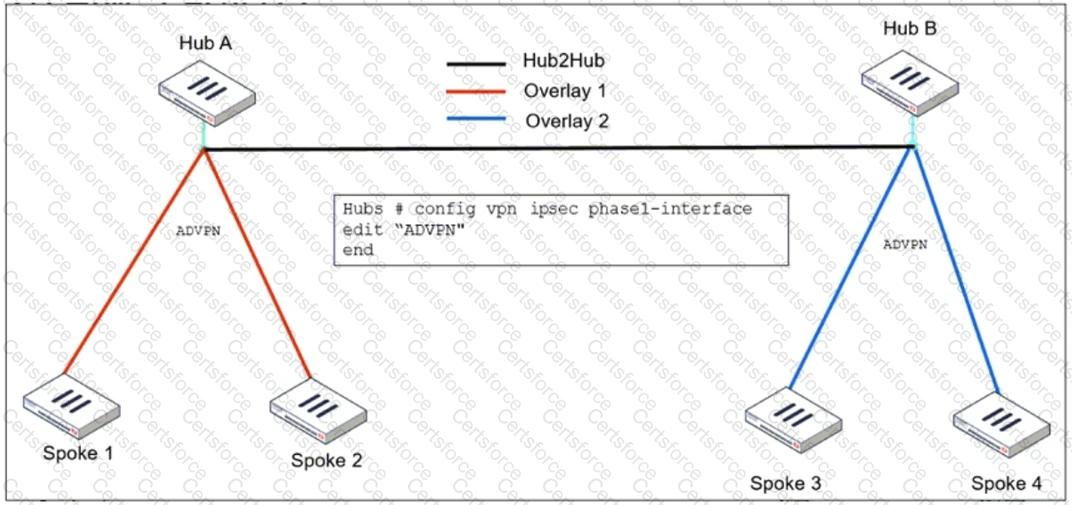
An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with 2.
What must the administrator configure in the phase 1 VPN IPsec configuration of the ADVPN tunnels?
Refer to the exhibit, which shows a physical topology and a traffic log.
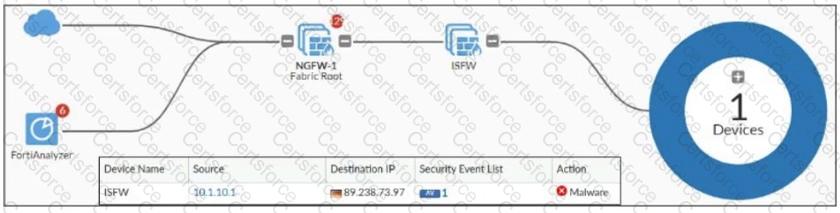
The administrator is checking on FortiAnalyzer traffic from the device with IP address 10.1.10.1, located behind the FortiGate ISFW device.
The firewall policy in on the ISFW device does not have UTM enabled and the administrator is surprised to see a log with the action Malware, as shown in the exhibit.
What are the two reasons FortiAnalyzer would display this log? (Choose two.)
What does the command set forward-domain