Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
Refer to the exhibit.
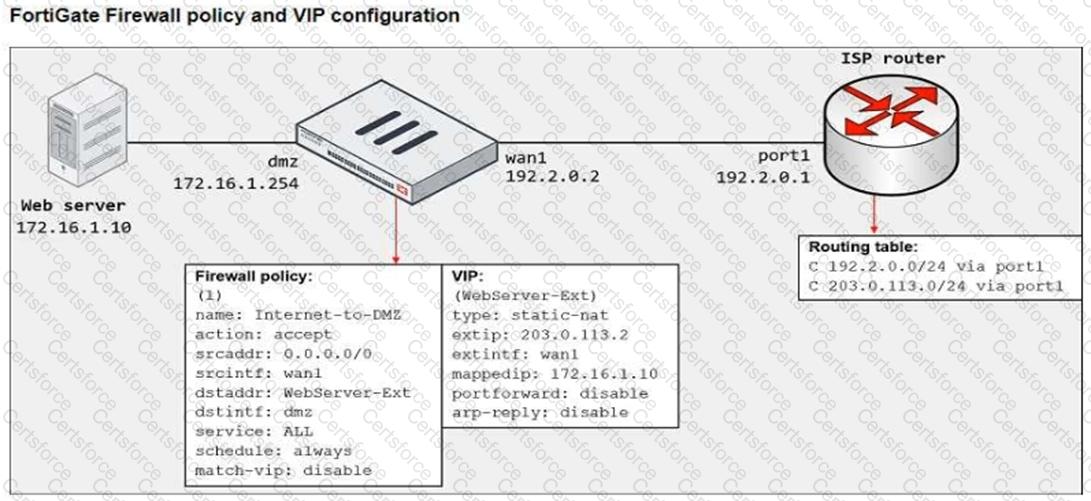
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
Refer to the exhibits.
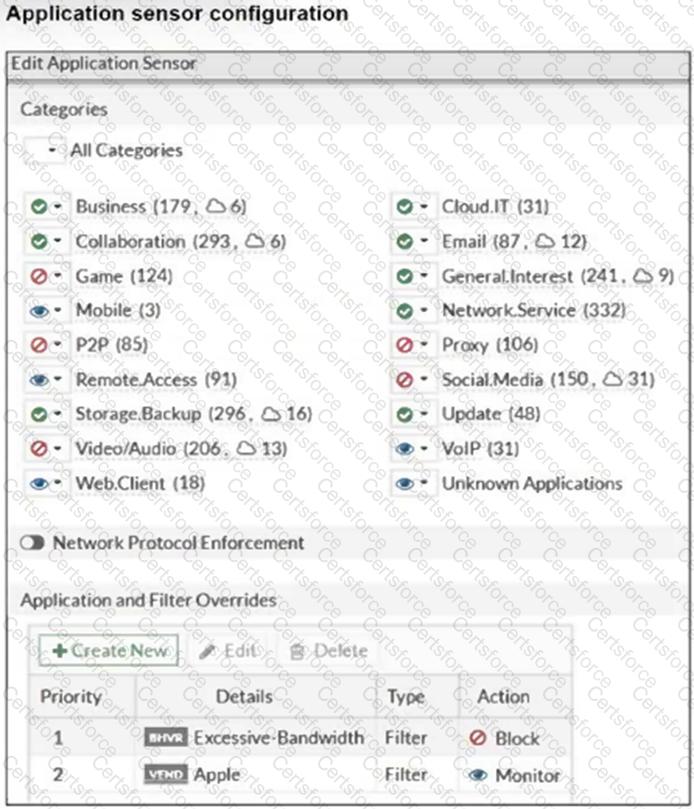
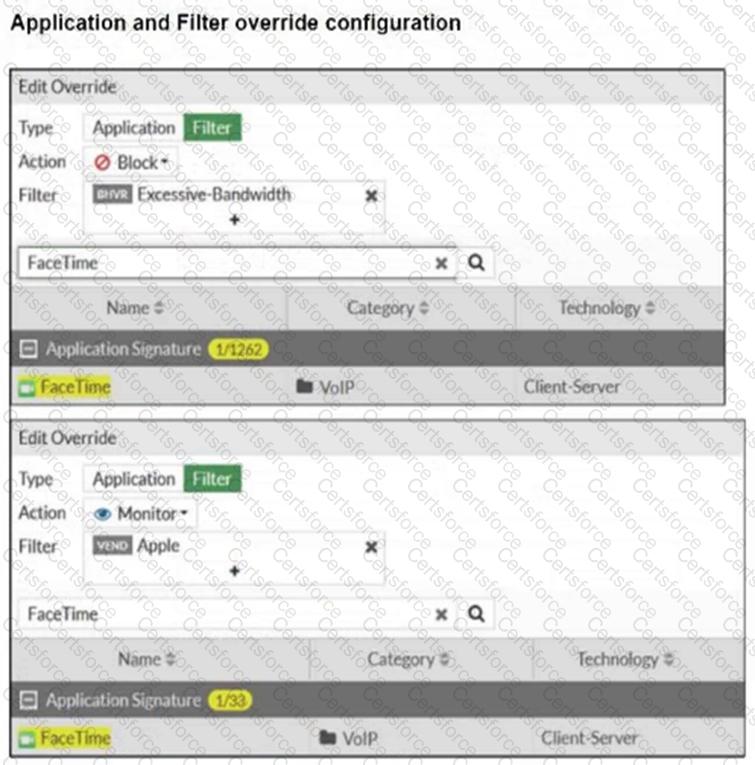
The exhibits show the application sensor configuration and theExcessive-BandwidthandApplefilter details.
Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming?
A network administrator is configuring an IPsec VPN tunnel for a sales employee travelling abroad.
Which IPsec Wizard template must the administrator apply?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
An administrator has configured the following settings:
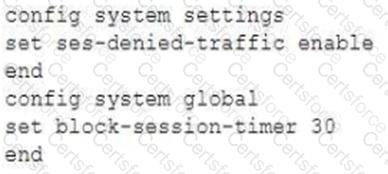
What are the two results of this configuration? (Choose two.)
Refer to the exhibit showing a debug flow output.
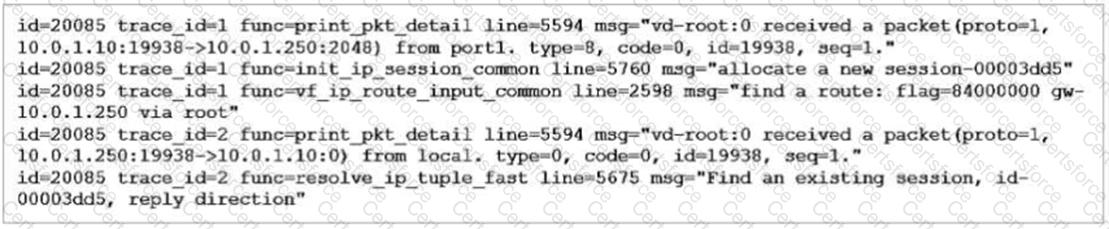
What two conclusions can you make from the debug flow output? (Choose two.)
Which two statements explain antivirus scanning modes? (Choose two.)
Which inspection mode does FortiGate use for application profiles if it is configured as a profile-based next-generation firewall (NGFW)?
How can you disable RPF checking?