The Backup Recovery Plan is dependent on what effort?
The CSIRT team is following the existing recovery plans on non-production systems in a PRE-BREACH
scenario. This action is being executed in which function?
What is the main goal of a gap analysis in the Identify function?
Refer to the exhibit.
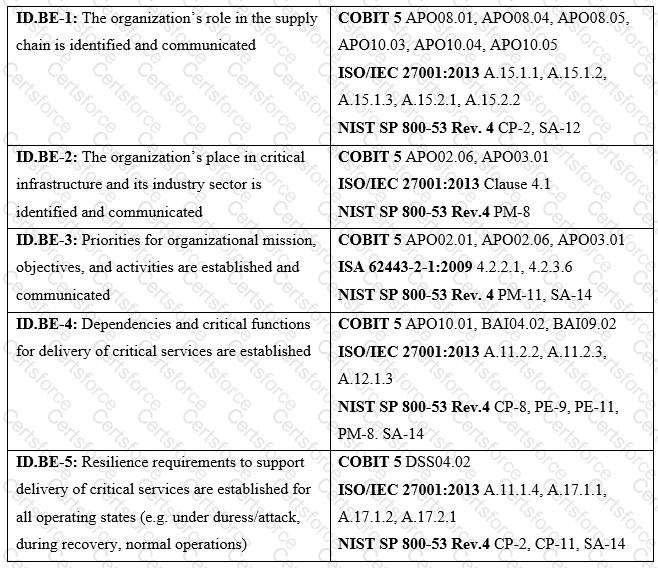
What type of item appears in the second column of the table?
Your data center uses a diesel generator as backup for two different power grids provided by your regional power company. During a period of unprecedented heat, you experience brown-outs on both grids simultaneously. The diesel generator starts up but only runs for two minutes before it also shuts down, leaving your entire data center down until grid power can be restored. Further inspection reveals a clogged fuel filter.
Failing to schedule preventive service for the backup generator is a failure in which function?
The network security team in your company has discovered a threat that leaked partial data on a compromised file server that handles sensitive information. Containment must be initiated and addresses by the CSIRT.
Service disruption is not a concern because this server is used only to store files and does not hold any critical workload. Your company security policy required that all forensic information must be preserved.
Which actions should you take to stop data leakage and comply with requirements of the company security policy?
What is concerned with availability, reliability, and recoverability of business processes and functions?
Your organization was breached. You informed the CSIRT and they contained the breach and eradicated the threat.
What is the next step required to ensure that you have an effective CSRL and a more robust cybersecurity posture in the future?