A CISO is looking for a solution to lower costs, enhance overall efficiency, and improve the reliability of
monitoring security related information.
Which ISCM feature is recommended?
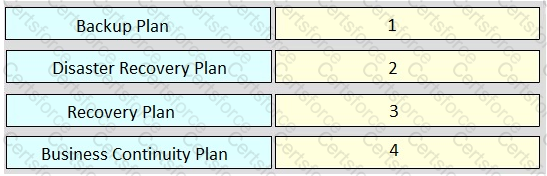
Rank order the relative severity of impact to an organization of each plan, where “1” signifies the most impact and “4” signifies the least impact.
What is the purpose of separation of duties?
What procedure is designed to enable security personnel to detect, analyze, contain, eradicate, respond, and
recover from malicious computer incidents such as a denial-of-service attack?
Your organization has tasked you with collecting information on all the data, personnel, devices, systems, and facilities that enable the organization to achieve its business purposes.
Which part of the NIST Cybersecurity Framework would you consult first?
What contains a predefined set of instructions or processes that describes the management policy,
procedures, and written plan defining recovery of information systems?
What process is used to identify an organization’s physical, digital, and human resource, as required in their Business Impact Analysis?
Your firewall blocked several machines on your network from connecting to a malicious IP address. After
reviewing the logs, the CSIRT discovers all Microsoft Windows machines on the network have been affected based on a newly published CVE.
Based on the IRP, what should be done immediately?
A company suffers a data breach and determines that the threat actors stole or compromised 10,000 user
profiles. The company had planned for such a breach and determined the loss would be around $2 million.
Soon after restoration, the company stock suffered a 30% drop and the loss was nearly $20 million. In addition, the company received negative press.
Which area of risk did the business forget to account for?
During what activity does an organization identify and prioritize technical, organizational, procedural,
administrative, and physical security weaknesses?