Which task describes adherence to compliance?
What capability does an orchestration workflow provide?
What term refers Amount of time and effort required to exploit an attack vector
In which technique does an application maintain limited functionality, even when some of the modules or supporting services of that application become unavailable?
What is an advantage of adopting a microservices strategy in an application development environment?
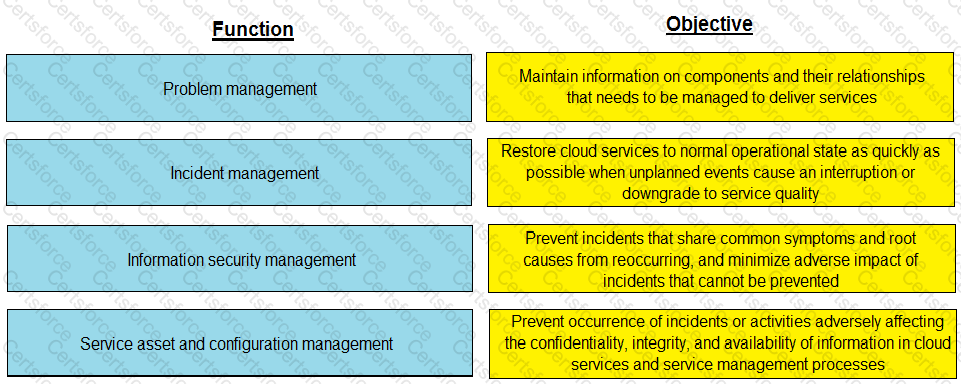
Match each key functions of service operation management with its objective.
Which phase of the cloud service lifecycle involves ongoing management activities to maintain cloud infrastructure and deployed services?
What is a benefit of the active-active cluster implementation?
An organization wants to deploy performance sensitive applications to meet their business requirements. Which type of storage device is suitable?
A specific intrusion detection and prevention system (IDPS) scans events against known attack patterns. Which technique is the IDPS using?