Which VM file is used to keep a record of the VM's activity and is often used for troubleshooting?
In a RAID 6 array with four disks, what is the total usable data storage capacity on the array if the disk size is 200 GB?
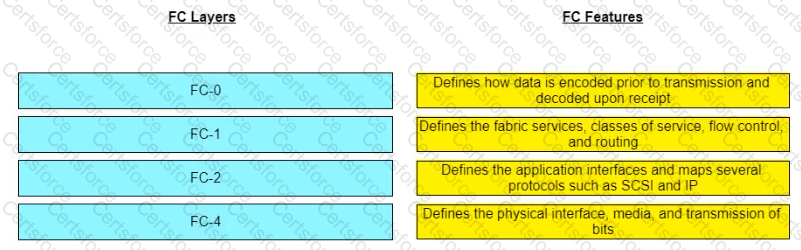
Match the Fibre Channel (FC) layers with their respective features.
What statement describes machine learning?
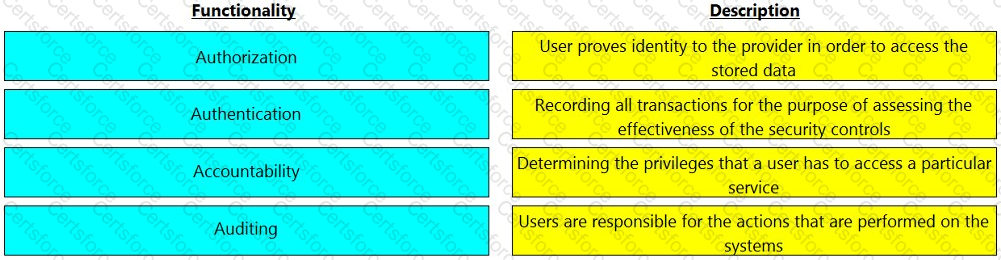
Match the functionality of a security goal with its description.
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
What is true about storage system-based replication?
What is a benefit of including a Defense-in-depth strategy as part of the data center security strategy?
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called'?
Which network file sharing protocol provides cloud-based file sharing through a REST API interface?