What will the following command accomplish?
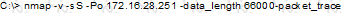
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set. What is Terri trying to accomplish by sending this IP packet?
You are working in the security Department of law firm. One of the attorneys asks you about the topic of sending fake email because he has a client who has been charged with doing just that. His client alleges that he is innocent and that there is no way for a fake email to actually be sent. You inform the attorney that his client is mistaken and that fake email is possibility and that you can prove it. You return to your desk and craft a fake email to the attorney that appears to come from his boss. What port do you send the email to on the company SMTP server?
What should you do when approached by a reporter about a case that you are working on or have worked on?
Profiling is a forensics technique for analyzing evidence with the goal of identifying the perpetrator from their various activity. After a computer has been compromised by a hacker, which of the following would be most important in forming a profile of the incident?
During the course of a corporate investigation, you find that an Employee is committing a crime. Can the Employer file a criminal complain with Police?
Diskcopy is:
The use of warning banners helps a company avoid litigation by overcoming an employees assumed
____________ When connecting to the company‟s intranet, network or Virtual Private Network(VPN) and will allow the company‟s investigators to monitor, search and retrieve information stored within the network.
One way to identify the presence of hidden partitions on a suspect‟s hard drive is to:
A state department site was recently attacked and all the servers had their disks eraseD. The incident response team sealed the area and commenced investigation. During evidence collection they came across a zip disks that did not have the standard labeling on it. The incident team ran the disk on an isolated system and found that the system disk was accidentally eraseD. They decided to call in the FBI for further investigation. Meanwhile, they short listed possible suspects including three summer interns. Where did the incident team go wrong?