Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
What is the following command trying to accomplish?
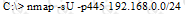
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
Larry is an IT consultant who works for corporations and government agencies. Larry plans on shutting down the city's network using BGP devices and ombies? What type of Penetration Testing is Larry planning to carry out?
What will the following URL produce in an unpatched IIS Web Server? 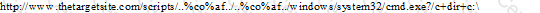
You are a security analyst performing reconnaissance on a company you will be carrying out a penetration test for. You conduct a search for IT jobs on Dice.com and find the following information for an open position:
7+ years experience in Windows Server environment
5+ years experience in Exchange 2000/2003 environment
Experience with Cisco Pix Firewall, Linksys 1376 router, Oracle 11i and MYOB v3.4 Accounting software are required MCSA desired,
MCSE, CEH preferred
No Unix/Linux Experience needed
What is this information posted on the job website considered?
After attending a CEH security seminar, you make a list of changes you would like to perform on your network to increase its security. One of the first things you change is to switch the RestrictAnonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server. Using Userinfo tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
A packet is sent to a router that does not have the packet destination address in its route table, how will the packet get to its properA packet is sent to a router that does not have the packet? destination address in its route table, how will the packet get to its proper destination?
An "idle" system is also referred to as what?
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive.org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code. While searching through the code, you come across something abnormal:
What have you found?