Oliver, a Server Administrator (Tomcat), has set configuration in web.xml file as shown in the following screenshot. What is he trying to achieve?

The software developer has implemented encryption in the code as shown in the following screenshot.
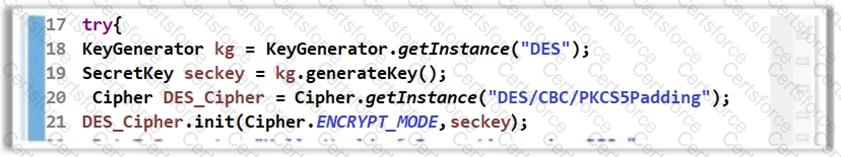
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?
Which of the following method will help you check if DEBUG level is enabled?
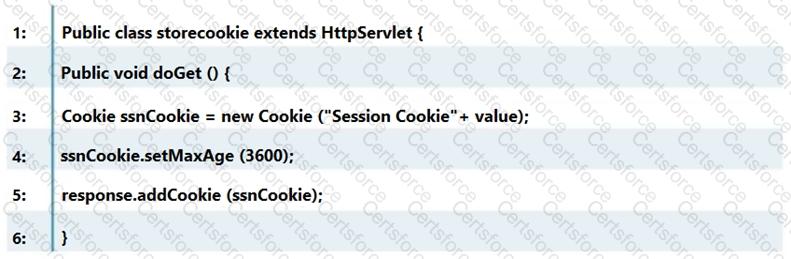
Which line of the following example of Java Code can make application vulnerable to a session attack?
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
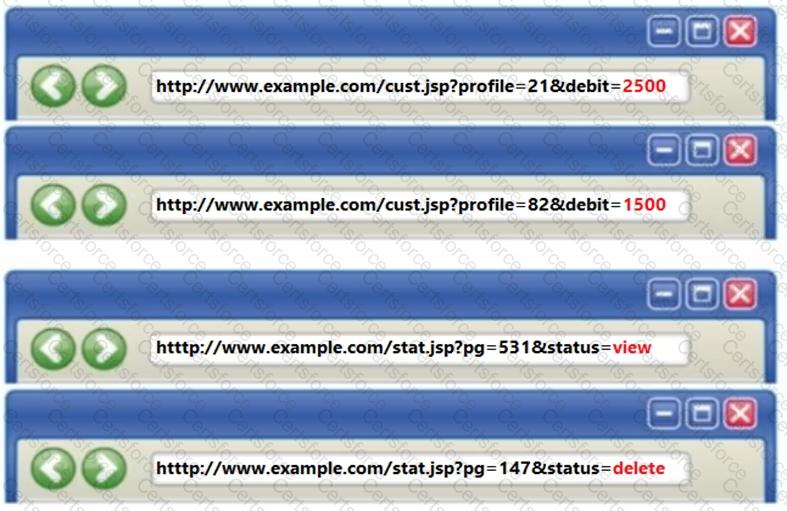
Identify the type of attack depicted in the following figure.
Which of the following is used to mapCustom Exceptions to Statuscode?
A US-based ecommerce company has developed their website www.ec-sell.com to sell their products online. The website has a feature that allows their customer to search products based on the price. Recently, a bug bounty has discovered a security flaw in the Search page of the website, where he could see all products from the database table when he altered the website URL http://www.ec-sell.com/products.jsp?val=100 to http://www.ec-sell.com/products.jsp?val=200 OR '1'='1 -. The product.jsp page is vulnerable to
Identify the formula for calculating the risk during threat modeling.
The threat modeling phase where applications are decomposed and their entry points are reviewed from an attacker's perspective is known as ________