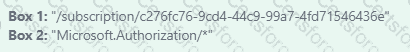
Box 1: "/subscription/c276fc76-9cd4-44c9-99a7-4fd71546436e"
In the assignableScopes you need to mention the subscription ID where you want to implement the RBAC
Box 2: "Microsoft.Authorization/*"
Microsoft.Authorization/* is used to Manage authorization
In Microsoft Azure Role-Based Access Control (RBAC), a custom role allows fine-grained permissions tailored to specific administrative needs. Custom RBAC roles are defined in JSON format and include three main elements — assignableScopes, permissions, and description.
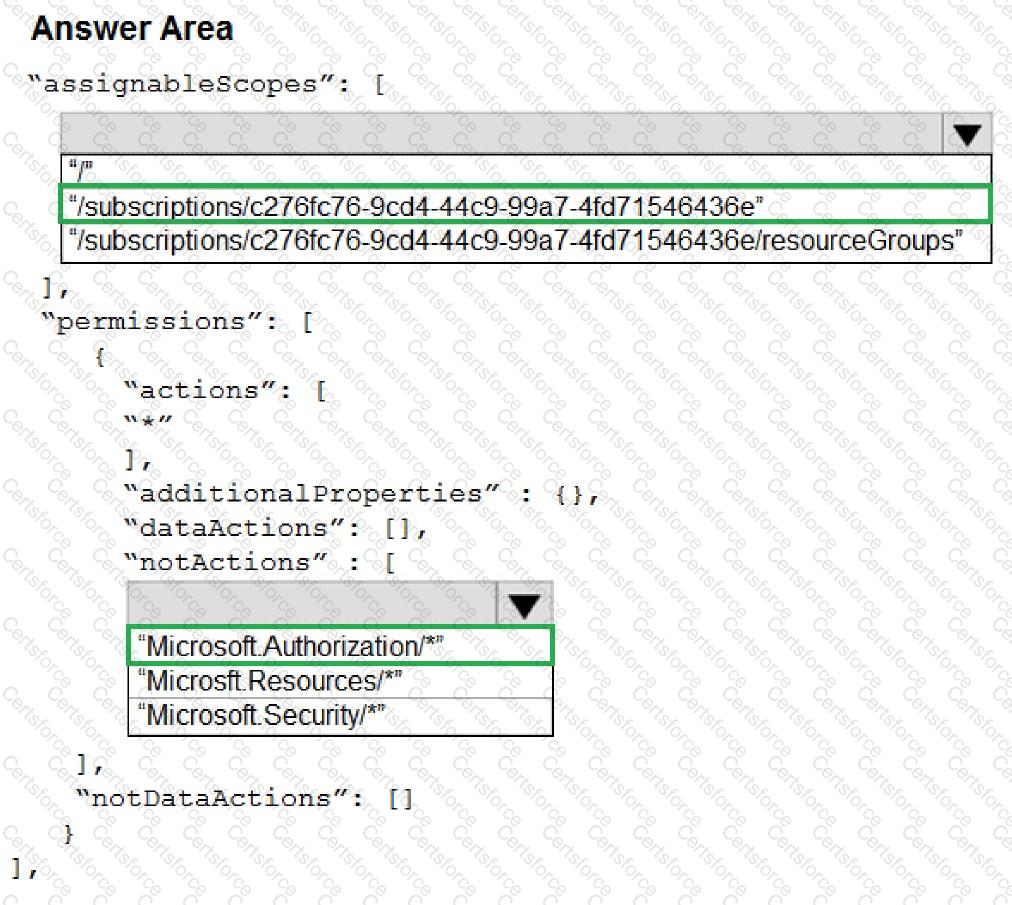
1. Assignable Scopes
The assignable scope defines where the custom role can be applied.
In this scenario, the role must only be assignable to resource groups in the given subscription (not at the subscription or tenant root level).
Therefore, the assignable scope should be limited to the resource groups path:
"/subscriptions/c276fc76-9cd4-44c9-99a7-4fd71546436e/resourceGroups"
This ensures that the role can be assigned only within resource groups in the specified subscription, not globally.
2. Permissions
The permissions section includes four arrays:
actions → defines allowed operations.
notActions → explicitly denies specific operations.
dataActions and notDataActions → for data-plane access (not needed here).
Because the requirement states that the user should be able to view, create, modify, and delete resources within the resource groups, the actions array should contain:
"actions": ["*"]
This grants full control over resource operations.
However, the question also specifies that the role must prevent the management of access permissions for the resource groups.
Managing access permissions is controlled by Microsoft.Authorization/ actions (e.g., Microsoft.Authorization/*/Write).
Thus, to explicitly block the ability to manage permissions, the notActions array must include:
"notActions": [
"Microsoft.Authorization/*"
]
This restriction ensures that users with this role cannot assign roles, modify access control (RBAC), or change role assignments, even though they have full resource management permissions otherwise.
3. Summary of Correct JSON Configuration
{
"Name": "CR1",
"Description": "Custom role to manage resources within resource groups but not RBAC permissions",
"AssignableScopes": [
"/subscriptions/c276fc76-9cd4-44c9-99a7-4fd71546436e/resourceGroups"
],
"Permissions": [
{
"Actions": [
"*"
],
"NotActions": [
"Microsoft.Authorization/*"
],
"DataActions": [],
"NotDataActions": []
}
]
}
4. Validation with Azure Administrator Study Guide
This configuration directly aligns with guidance in Microsoft Learn: “Azure custom roles in Azure RBAC” and AZ-104 Study Guide Module: Manage role-based access control (RBAC).
It meets all requirements:
Restricts role assignment scope to resource groups only.
Allows full resource management (CRUD).
Denies RBAC access control modifications via Microsoft.Authorization/*.
Final Verified Answers:
✅ Assignable Scope: /subscriptions/c276fc76-9cd4-44c9-99a7-4fd71546436e/resourceGroups
✅ Permission (notActions): "Microsoft.Authorization/*"
Submit