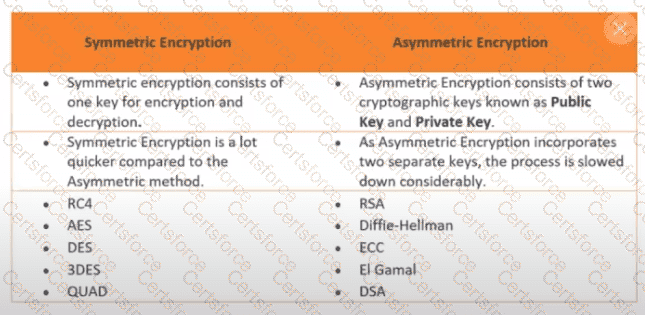
In anasymmetric cryptography system, each user is assigned akey pairconsisting ofone public key and one private key. These two keys are mathematically related but serve different purposes: the public key is shared openly for encryption or verification, while the private key is kept secret for decryption or signing.
To support50 users, each user must have2 keys:
1 public key
1 private key
Therefore, the total number of keys required is:
50 users × 2 keys per user = 100 keys
This is one of the major advantages of asymmetric cryptography over symmetric cryptography. In symmetric systems, the number of required keys grows rapidly as the number of users increases (n(n−1)/2), making key management complex. Asymmetric cryptography scales much more efficiently because each user manages only their own key pair.
Asymmetric encryption is widely used in secure communications such as TLS, digital signatures, and PKI-based authentication. Standards bodies like NIST and ISO/IEC rely heavily on asymmetric cryptography for scalable and secure key management.
Submit