
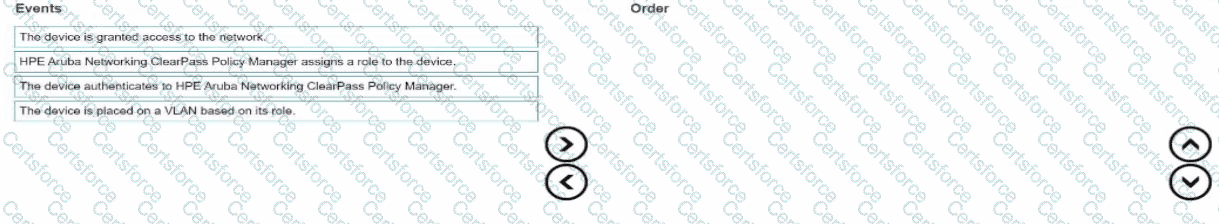
This question asks for the sequence of events when a user device connects to a network utilizing Dynamic Segmentation, which typically involves authentication via ClearPass and role-based policy assignment.
Authentication:When a device connects (wired or wireless), the first step in gaining secure access is authentication. The switch or AP (authenticator) facilitates this process, usually communicating via RADIUS with ClearPass Policy Manager (RADIUS server). The device provides credentials or uses certificates (e.g., 802.1X, MAC Auth).
Role Assignment:Upon successful authentication, ClearPass evaluates policies based on the device/user context (identity, posture, time of day, etc.) and sends back RADIUS attributes to the authenticator. A crucial attribute is the assigned User Role. This role encapsulates the access privileges and network configuration for the device.
Network Placement/Segmentation:The authenticator (switch/AP) uses the assigned role information received from ClearPass to place the device into the appropriate network segment. This might involve assigning a specific VLAN ID to the port/client or, in User-Based Tunneling (UBT) scenarios, establishing a tunnel to an Aruba Gateway associated with that role. The step "placed on a VLAN based on its role" describes one common method of segmentation based on the assigned role.
Access Granted:Once the device is authenticated, assigned a role, and placed in the correct network segment (VLAN or tunnel), access is granted according to the firewall rules, QoS settings, and other policies defined within that assigned role. Traffic can now flow subject to these enforced policies.
[References:Aruba Dynamic Segmentation Solution Guides, ClearPass Policy Manager Documentation, AOS-CX Security Guide (Roles, Port Access). This relates to "Authentication/Authorization" (9%), "Security" (10%), "Switching" (19%), and "WLAN" (9%) objectives., , ]
Submit