 A screenshot of a computer
Description automatically generated
A screenshot of a computer
Description automatically generated
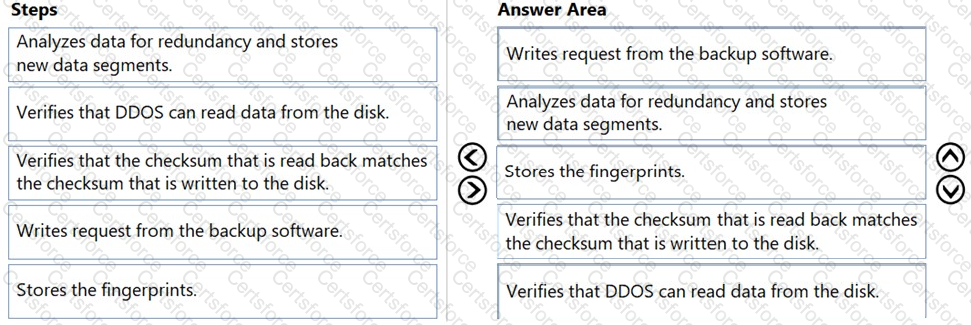
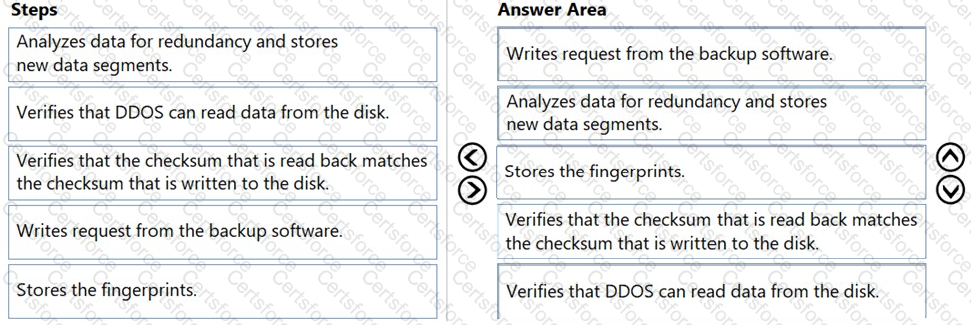
1. Writes request from the backup software
First, the backup software sends a write request to the DD system.
2. Analyzes data for redundancy and stores new data segments
Next, DDOS analyzes the incoming data for redundancy and stores only the unique data segments to optimize storage.
3. Stores the fingerprints
After deduplication, the system stores the unique fingerprints of the data.
4. Verifies that the checksum that is read back matches the checksum that is written to the disk
This step involves verifying the data integrity by matching the written checksum with the read checksum.
5. Verifies that DDOS can read data from the disk
Finally, the system verifies that the data can be read back correctly from the disk, ensuring the write was successful.
Submit