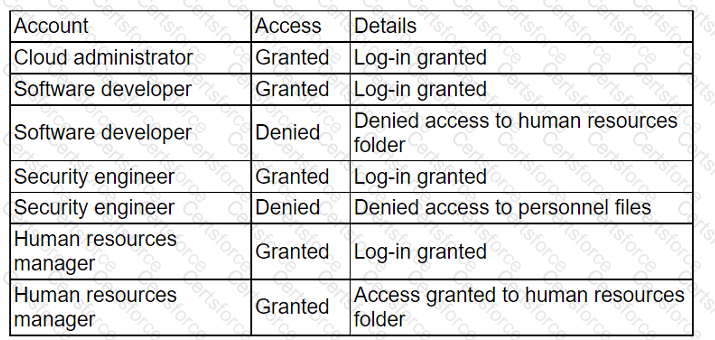
An administrator received a report that company data has been compromised. The compromise occurred on a holiday, and no one in the organization was working. While reviewing
the logs from the holiday, the administrator noted the following details:
The most appropriate action for the cloud security analyst to recommend is using CIS-hardened images. These images are pre-configured by the Center for Internet Security to provide security benchmark standards that help in mitigating vulnerabilities in publicly available container images. References: CompTIA Cloud+ Study Guide (Exam CV0-004) - Chapter on Cloud Security Posture
Which of the following accounts should the administrator disable to prevent a further breach?
The company's IDS has reported an anomaly. The cloud engineer remotely accesses the cloud instance, runs a command, and receives the following information:
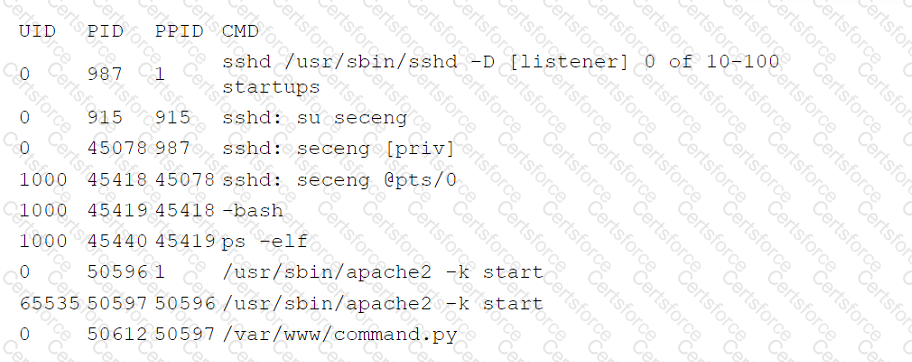
Which of the following is the most likely root cause of this anomaly?
A cloud engineer is collecting web server application logs to troubleshoot intermittent issues. However, the logs are piling up and causing storage issues. Which of the following log
mechanisms should the cloud engineer implement to address this issue?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
A banking firm's cloud server will be decommissioned after a successful proof of concept using mirrored data. Which of the following is the best action to take regarding the storage used on the decommissioned server?
A cloud solutions architect is designing a VM-based solution that requires reducing the cost as much as possible. Which of the following solutions will best satisfy this requirement?
A cloud developer receives a security vulnerability scan report and needs to analyze and record the true positives. Which of the following vulnerability management steps is this an example of?
Which of the following requirements are core considerations when migrating a small business's on-premises applications to the cloud? (Select two).
A cloud solution needs to be replaced without interruptions. The replacement process can be completed in phases, but the cost should be kept as low as possible. Which of the
following is the best strategy to implement?
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage. Which of the following
best describes the nature of the local storage?