You have determined that the company Web server has several vulnerabilities, including a buffer overflow that has resulted in an attack. The Web server uses PHP and has direct connections to an Oracle database server. It also uses many CGI scripts. Which of the following is the most effective way to respond to this attack?
Consider the following diagram:
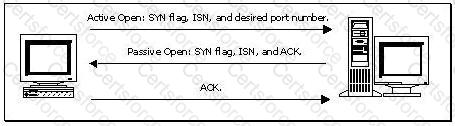
Which of the following best describes the protocol activity shown in the diagram, along with the most likely potential threat that accompanies this protocol?
What is the primary drawback of using symmetric-key encryption?
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
The best way to thwart a dictionary attack is by enforcing a:
An application is creating hashes of each file on an attached storage device. Which of the following will typically occur during this process?
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
Which of the following applications can help determine whether a denial-of-service attack is occurring against a network host?
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?