A Cisco PoE switch is shown in the following image. Which type of port will provide both data connectivity and power to an IP phone?

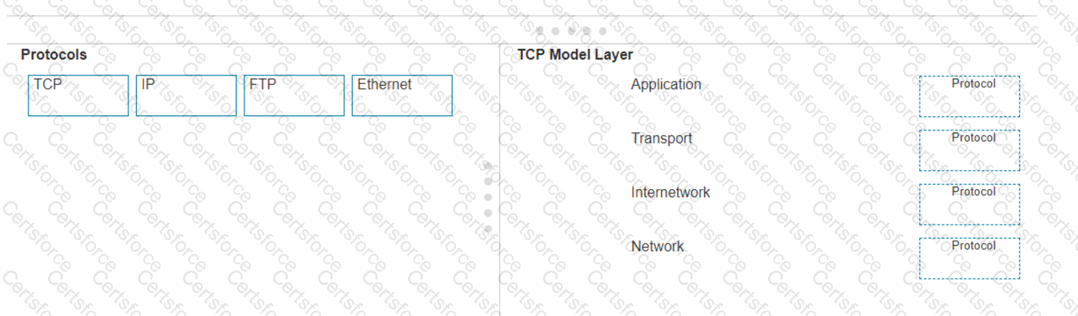
Move each protocol from the list on the left to the correct TCP/IP model layer on the right.
Note: You will receive partial credit for each correct match.
A Cisco switch is not accessible from the network. You need to view its running configuration.
Which out-of-band method can you use to access it?
What is the most compressed valid format of the IPv6 address 2001 :0db8:0000:0016:0000:001b: 2000:0056?
Computers in a small office are unable to access companypro.net. You run the ipconfig command on one of the computers. The results are shown in the
exhibit.
You need to determine if you can reach the router.
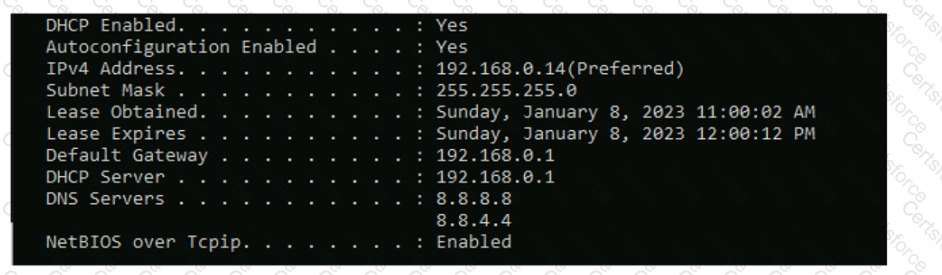
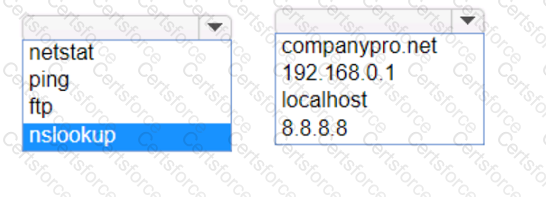
Which command should you use? Complete the command by selecting the correct options from each drop-down lists.
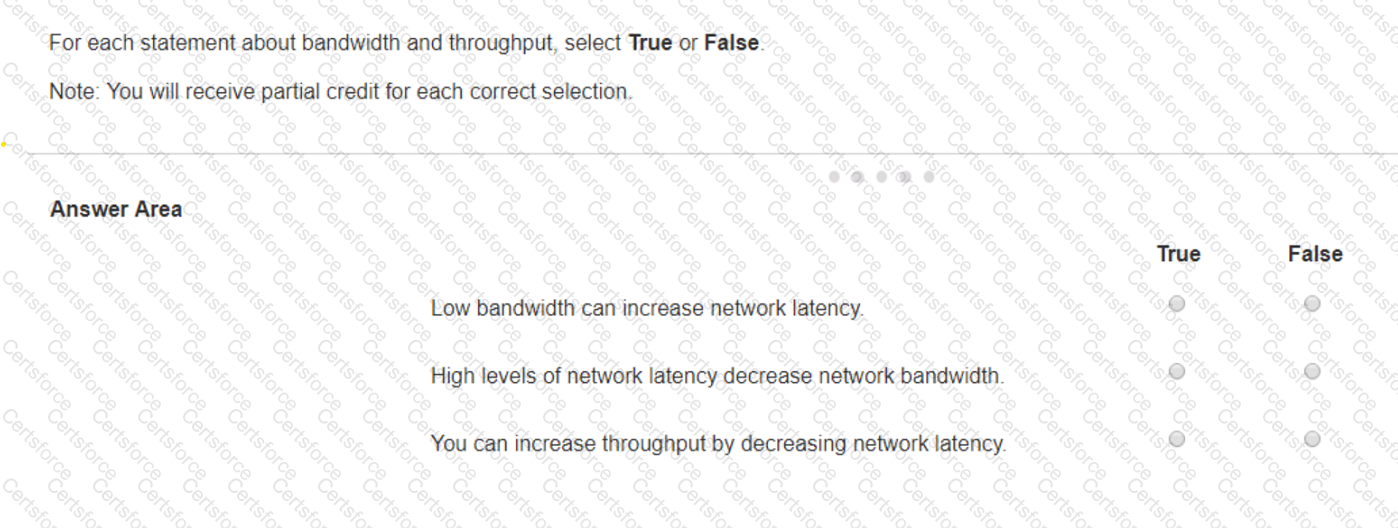
For each statement about bandwidth and throughput, select True or False.
Note: You will receive partial credit for each correct selection.
You purchase a new Cisco switch, turn it on, and connect to its console port. You then run the following command:
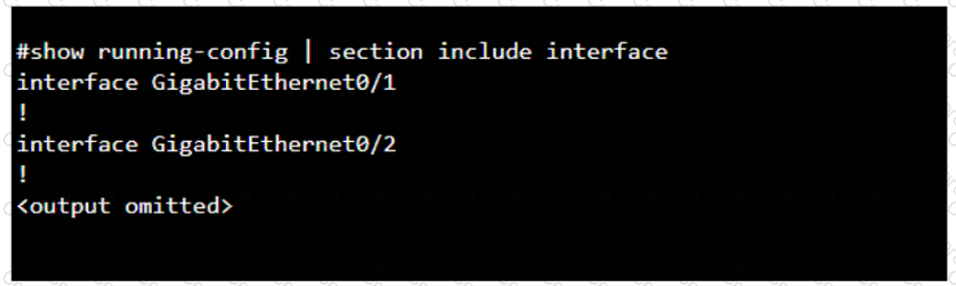
For each statement about the output, select True or False.
Note: You will receive partial credit for each correct selection.
Move each network type from the list on the left to the correct example on the right.
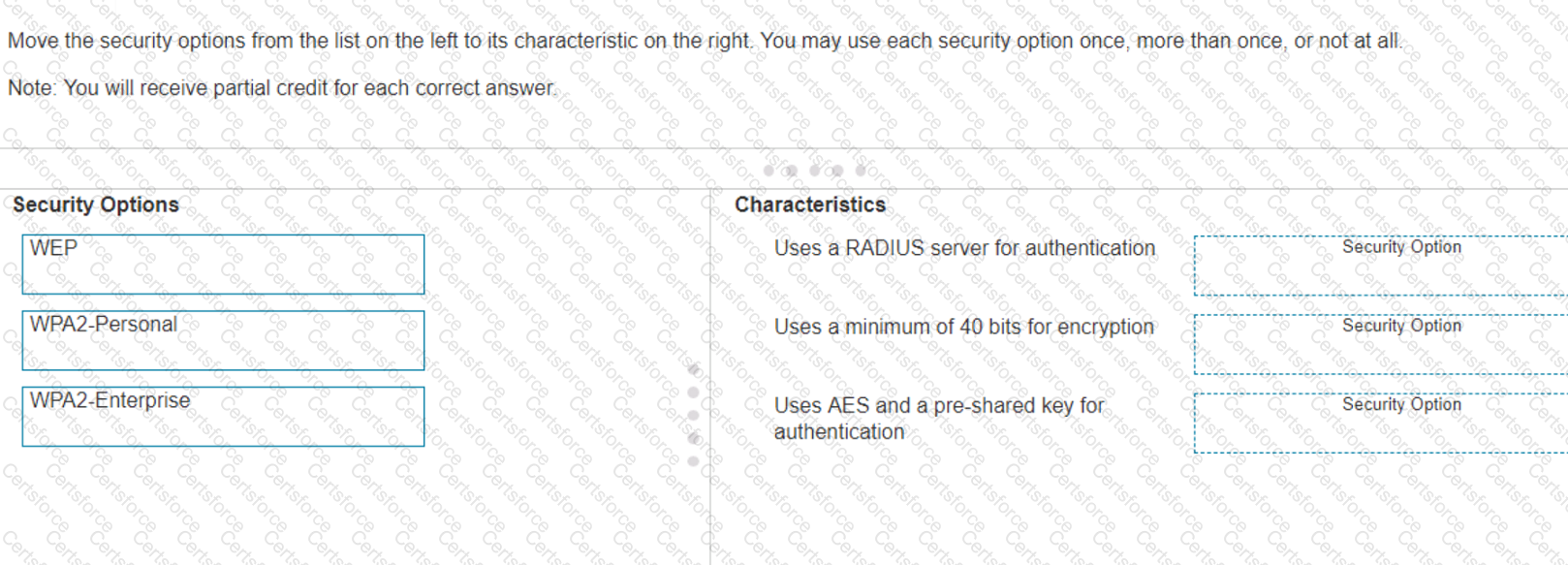
Move the security options from the list on the left to its characteristic on the right. You may use each security option once, more than once, or not at all.
Note: You will receive partial credit for each correct answer.
During the data encapsulation process, which OSI layer adds a header that contains MAC addressing information and a trailer used for error checking?