Refer to the exhibit.
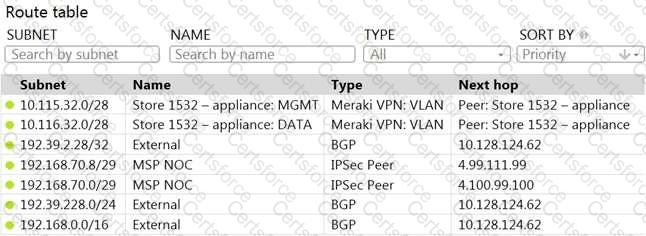
A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4.
What is the next hop for the packet, based on this concentrator routing table?
An organization requires that BYOD devices be enrolled in Systems Manager before they gain access to the network. Part of the enrollment includes pushing out the corporate SSID preshared key, corporate email settings, and some business-sensitive PDFs. When a user leaves the organization, which Systems Manager feature allows the removal of only the MDM-delivered content from the user's device?
Which two actions can extend the video retention of a Cisco Meraki MV Smart Camera? (Choose two.)
Refer to the exhibit.

Which outcome occurs when logging is set to Enabled?
For which two reasons can an organization become “Out of License”? (Choose two.)
What are two methods of targeting and applying management profiles to System Manager clients? (Choose two.)
The WAN connection of a Cisco Meraki MX security appliance is congested, and the MX appliance is buffering the traffic from LAN ports going to the WAN ports. High, normal, and low priority queue buffers are all full. Which proportion of the normal traffic is forwarded compared to the other queues?
Which type of authentication protocol is used when using OSPF on an MX appliance?
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
There will be 100 concurrent users streaming video to their laptops. A 30/70 split between 2.4 Ghz and 5 Ghz will be used. Roughly how many APs (rounded to the nearest whole number) are needed based on client count?