What is a risk to data privacy during the storage and transmission of data?
Which Git command enables the developer to revert back to f414f31 commit to discard changes in the current working tree?
What are two advantages of using model-driven telemetry, such as gRPC. instead of traditional telemetry gathering methods? (Choose two.)
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
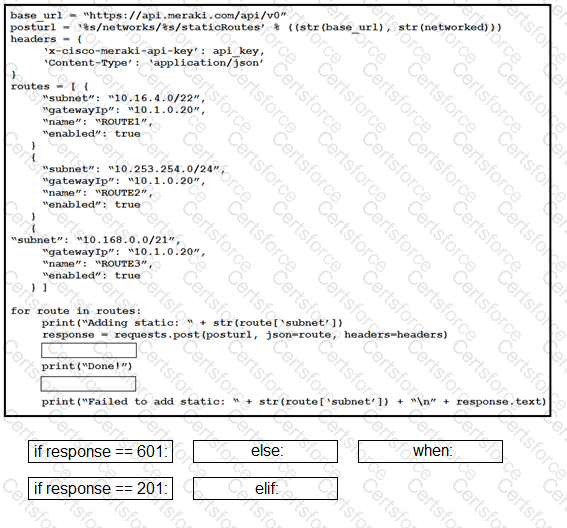
Refer to the exhibit.
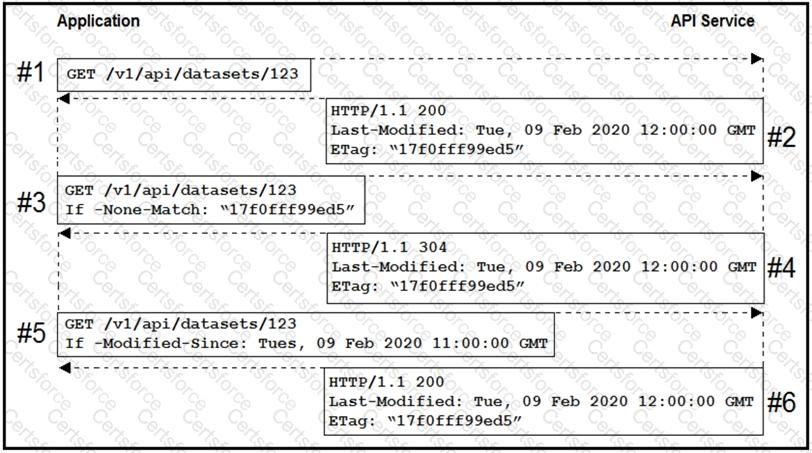
An application uses an API to periodically sync a large data set. Based on the HTTP message sequence provided, which statements are true about the caching behavior seen in the scenario? (Choose two.)
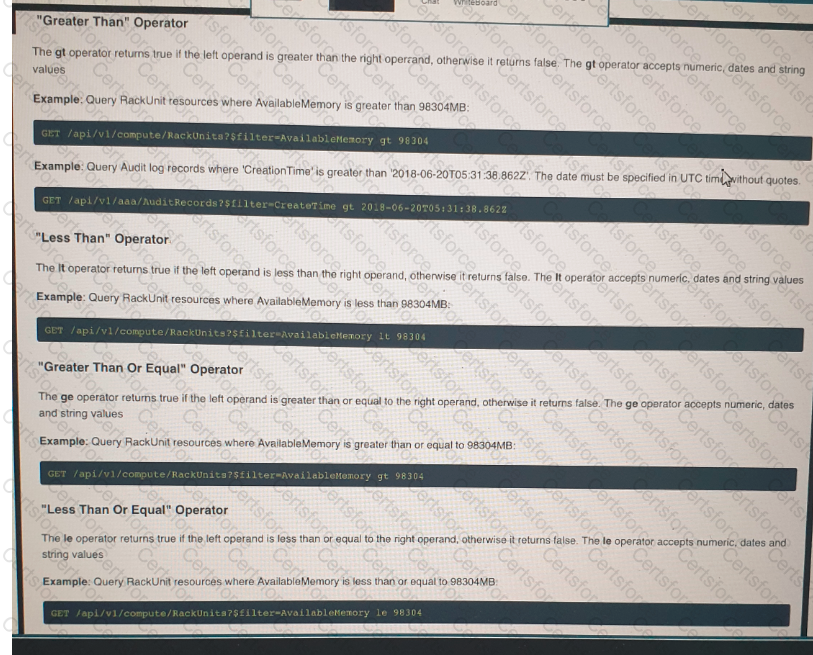
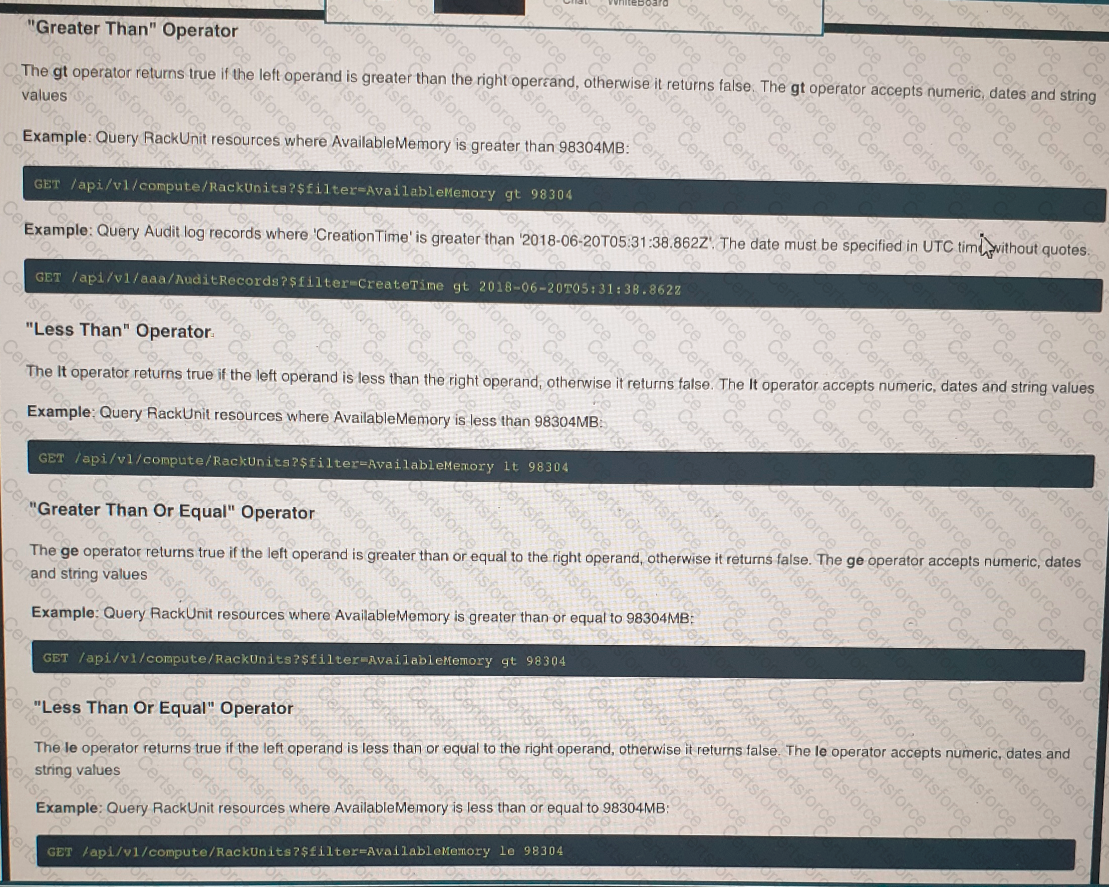
Click on the GET Resource button above to view resources that will help with this question. An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
An engineer is developing a Docket container for an application in Python For security reasons the application needs to be accessible on port 5001 only Which line should be added to the dockerfile m order to accomplish this?
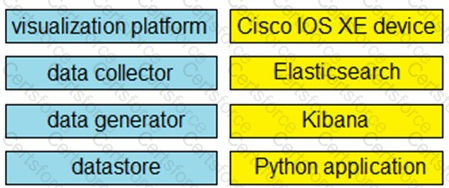
A Python application is being written to run inside a Cisco IOS XE device to assist with gathering telemetry data. Drag and drop the elements of the stack from the left onto the functions on the right to collect and display the telemetry streaming data.
A developer must deploy a containerized application for network device inventory management. The developer sets up a Kubernetes cluster on two separate hypervisors The SLA is not currently meeting a specified maximum value for network latency/jitter. CPU/memory and disk 1,0 are functioning property.
Which two design approaches resolve the issue? (Choose two.)
Which action enhances end-user privacy when an application is built that collects and processes the location data from devices?