An IT department needs to deploy a new application named ‘Entfin434772390’ across the entire enterprise. The deployment must gradually transfer user traffic from an on older and nearly identical version of the application named ‘Entfin02754932l’. Both versions of the application are running in the production environment.
Which release strategy should be used by the IT department?
A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of “Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?
A development team is using Cl/CD during application development During the latest releases runtime vulnerabilities have been indicated to address these vulnerabilities. a complete redesign oí the affected applications were required To overcome this issue black box testing has been proposed. What must be used to automate this testing within a Cl/CD pipeline.
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
What is the impact of using the Drone.io CI/CD tool on the local installation step?
Refer to the exhibit.

The text represents a syslog message sent from a Linux server to a centralized log system.
Based on the format of the log message, how must the functionality of the log parser be extended to improve search capabilities?
Refer to the exhibit.
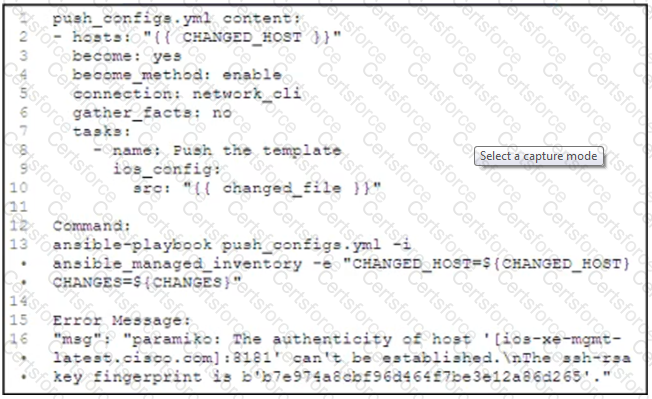
The push_configs.yml playbook returns the error shown.
Which action resolves the error?
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
What is a principle of chaos engineering?