An administrator must deploy an endpoint posture policy for all users. The organization wants to have all endpoints checked against antimalware definitions and operating system updates and ensure that the correct Secure Client modules are installed properly. How must the administrator meet the requirements?
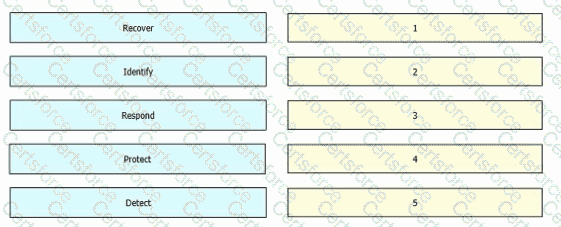
Drag and drop the five core functions from the left into the order defined by the NIST Cyber security Framework on the right.

Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to prevent restricted users from being able to browse any business or mobile phone shopping websites. The indicated policy was applied; however, the restricted users still can browse on the mobile phone shopping websites during business hours. What should be done to meet the requirement?
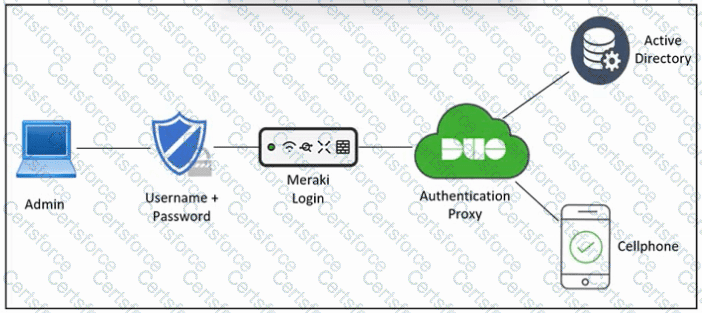
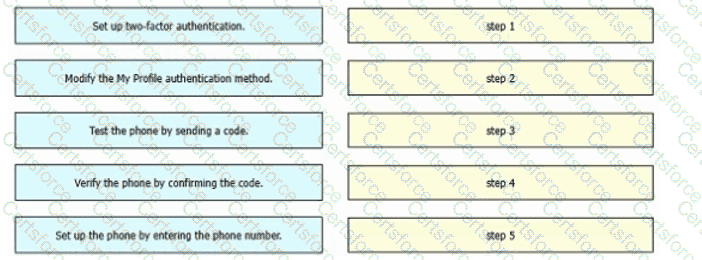
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile and received an activation code. Drag and drop the steps from left to right to complete the configuration.
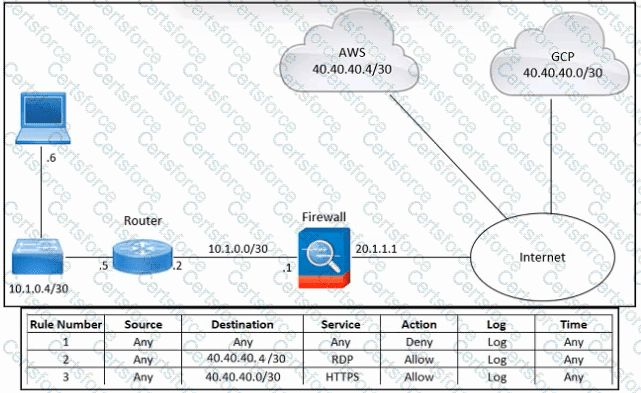
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?

Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv2 VPN that will use SHA-512 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which command must be run to meet the requirement?
According to Cisco Security Reference Architecture, which solution provides threat intelligence and malware analytics?
What does the MITRE ATT&CK framework catalog?