Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
An employee receives an email from a “trusted” person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads. An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance with the incident response plan. Which event detail should be included in this root cause analysis?
An analyst finds .xyz files of unknown origin that are large and undetected by antivirus. What action should be taken next?
Refer to the exhibit.
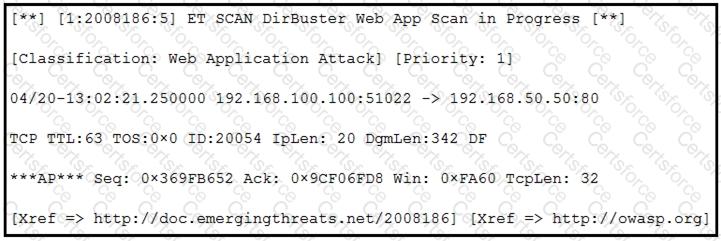
According to the SNORT alert, what is the attacker performing?
Refer to the exhibit.

Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
Refer to the exhibit.

An alert came with a potentially suspicious activity from a machine in HR department. Which two IOCs should the security analyst flag? (Choose two.)
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
A security team is notified from a Cisco ESA solution that an employee received an advertising email with an attached .pdf extension file. The employee opened the attachment, which appeared to be an empty document. The security analyst cannot identify clear signs of compromise but reviews running processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)