You are reviewing your company’s disaster recovery plan.
Which two daily data backup actions should the plan include?(Choose 2.)
How does a honeypot enhance network security?
Which macOS security feature encrypts the entire macOS volume?
You need to design your company’s password policy to adhere to the National Institute of Standards and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST guidelines?
You are planning to work from home. Your company requires that you connect to the company network through a VPN.
Which three critical functions do VPNs provide to remote workers?(Choose 3.)
Your supervisor suspects that someone is attempting to gain access to a Windows computer by guessing user account IDs and passwords. The supervisor asks you to use the Windows Event Viewer security logs to verify the attempts.
Which two audit policy events provide information to determine whether someone is using invalid credentials to attempt to log in to the computer?(Choose 2.)
Note: You will receive partial credit for each correct selection.
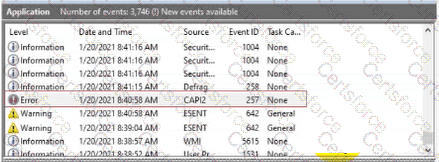
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
You notice that a new CVE has been shared to an email group that you belong to.
What should you do first with the CVE?
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a successful login to a privileged account. What is the most appropriate next step?
For each statement, selectTrueif it is a common motivation to commit cyber attacks orFalseif it is not.
Note: You will receive partial credit for each correct selection.
