Refer to the exhibit.
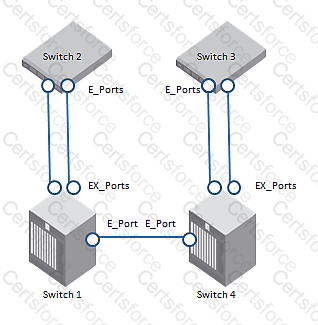
Referring to the exhibit, which two statements are true regarding FC-FC routing? (Choose two.)
Refer to the exhibit.
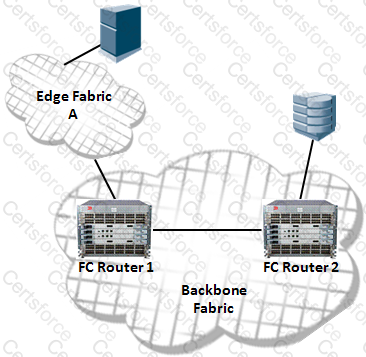
In the exhibit, the server and the storage are communicating in an operational metaSAN.
Which two statements are true? (Choose two.)
Refer to the exhibit.
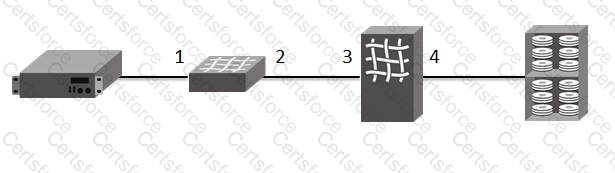
You need to enable Flow Mirror for a specific frame type between an initiator and a target.
Referring to the exhibit, where would you insert the Flow Mirror?
Your existing fabric has Brocade switches using Fabric OS v7.1 with Fabric Watch and Advanced Performance Monitor licenses already installed. You want to upgrade to v7.2 and run Flow Vision.
Which statement is true?
You want to monitor traffic between a virtual host and a specified LUN. Additionally, you want to have the switch send an e-mail to the administrator if the transmit bandwidth exceeds a certain threshold.
Which two steps will accomplish this task? (Choose two.)
A host and target pair are using over 50 percent of a 16 Gbps ISL. You want to prevent this pair from impacting the performance of other flows and proactively avoid congestion.
Which two methods would accomplish this goal? (Choose two.)
You want to capture real-time performance data for every port in the SAN.
Which tool would accomplish this task?
You have just run SAN Health Diagnostics Capture and SAN Health Professional.
Which three critical tasks can you perform based on this report? (Choose three.)
You are monitoring a flow using MAPS in Brocade Network Advisor.
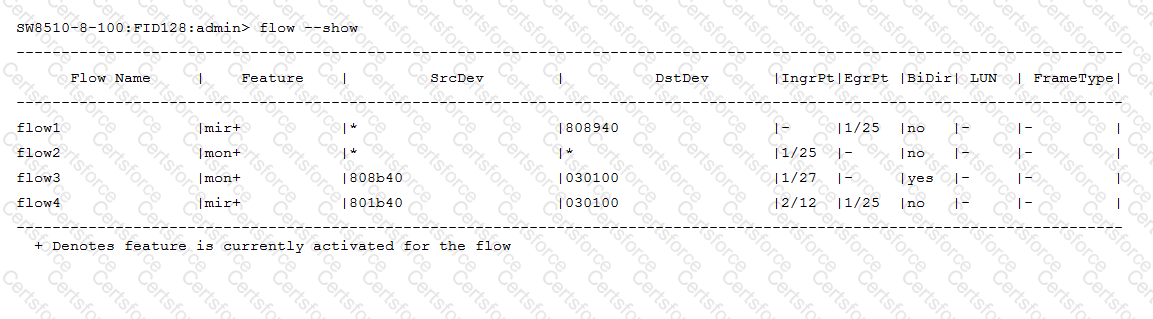
Referring to the exhibit, which two flows would be imported into MAPS? (Choose two.)
You need to collect encrypted data from your Brocade 6520.
Which two protocols would be used to do this task? (Choose two.)