Review the screenshot, and then answer the question below.
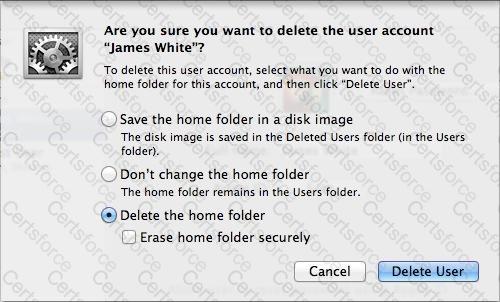
If you click Delete User in the dialog shown above, what will happen to James White's home folder?
Which statement is true of ALL THREE buses: USB, FireWire, AND Thunderbolt?
Which OS X Mountain Lion tool can help you create a strong password?
You can deselect the option to "Reopen windows when logging back in" from the logout verification dialog. You can deselect the option to "Close windows when quitting an application" from General preferences. Also from General preferences, you can select the option to "Ask to keep changes when closing documents," which turns off the Auto Save feature.
How is 802.1X configured on OS X systems?
Where are the keychain files stored?
How can you encrypt a disk without losing its contents?
Key chains are used to store secrets such as resource passwords, digital certificates, and encryption keys. The keychain system can also securely store Safari AutoFill information, Internet Account settings, and secure text notes.
What steps should you use when troubleshooting application issues?
Before the local user account is created on a system, you must first copy the restored user's home folder to the /Users folder. Then after you create the new user in Users &Groups preferences with the same account name, the system will prompt you to associate the new account with the restored home folder.