What are two reasons an administrator should utilize a manual configuration to determine the endpoint location? (Choose two.)
Which two factors are common sources of data leakage where the main actor is well-meaning insider? (Choose two.)
Which two DLP products support the new Optical Character Recognition (OCR) engine in Symantec DLP 15.0? (Choose two.)
Which two detection servers are available as virtual appliances? (Choose two.)
Which two Network Discover/Cloud Storage targets apply Information Centric Encryption as policy response rules?
A divisional executive requests a report of all incidents generated by a particular region, summarized by department.
What does the DLP administrator need to configure to generate this report?
An administrator is unable to log in to the Enforce management console as “sysadmin”. Symantec DLP is configured to use Active Directory authentication. The administrator is a member of two roles: “sysadmin” and “remediator.”
How should the administrator log in to the Enforce console with the “sysadmin” role?
Which channel does Endpoint Prevent protect using Device Control?
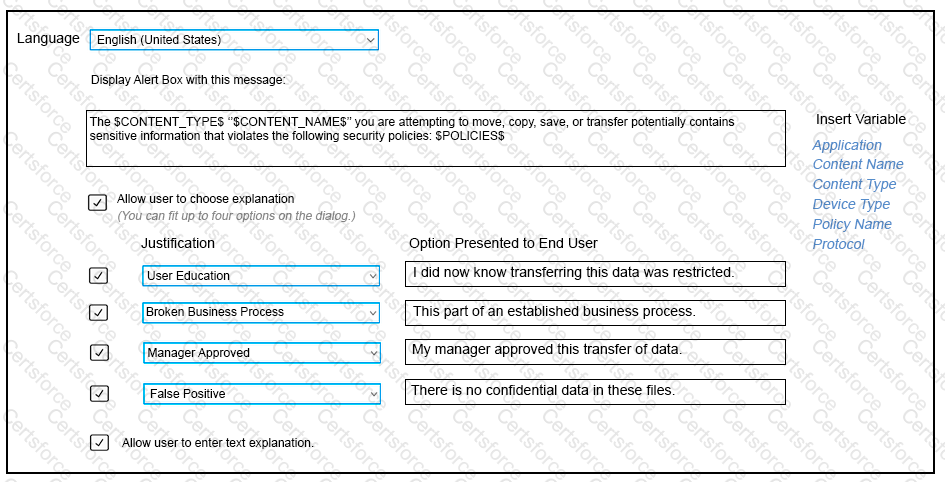
Refer to the exhibit. Which type of Endpoint response rule is shown?
Which tool must a DLP administrator run to certify the database prior to upgrading DLP?