A company wants to add threat prevention to the network without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
When you troubleshoot an SSL Decryption issue, which PAN-OS CL1 command do you use to check the details of the Forward Trust certificate. Forward Untrust certificate, and SSL Inbound Inspection certificate?
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile. What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
The UDP-4501 protocol-port is to between which two GlobalProtect components?
Which configuration change will improve network reliability and ensure minimal disruption during tunnel failures?
During a routine security audit, the risk and compliance team notices a series of WildFire logs that contain a "malicious" verdict and the action "allow." Upon further inspection, the team confirms that these same threats are automatically blocked by the firewalls the following day. How can the existing configuration be adjusted to ensure that new threats are blocked within minutes instead of having to wait until the following day?
Which two methods can be configured to validate the revocation status of a certificate? (Choose two.)
An administrator accidentally closed the commit window/screen before the commit was finished. Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
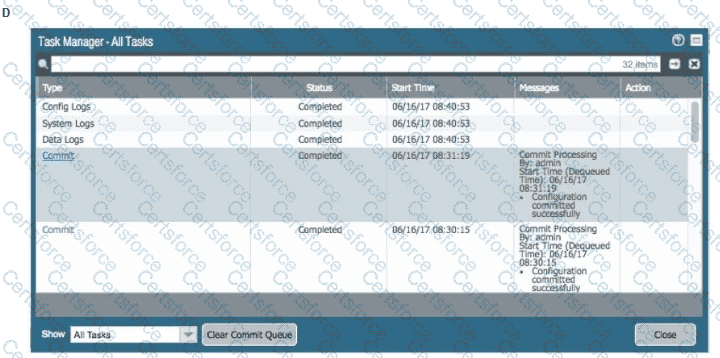
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install.
When performing an upgrade on Panorama to PAN-OS. what is the potential cause of a failed install?
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)