You Issue this statement as user SYS:
audit, context namespace kilimanjaro attributes a, b;
Which is true?
You develop an HR application that must allow multiple sessions to share application attributes. Which statement is executed while implementing the requirement?
Which type of attack attempts to find data by repeatedly trying similar SQL with a modified predicate?
You are connected to an Oracle database Instance as a user with privileges to query the hr.employees table.
You are not exempt from any reduction policies.
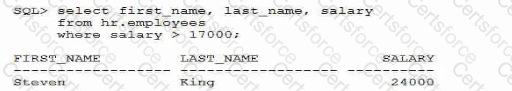
Examine this query and result:
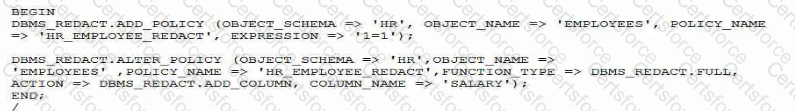
You implement this Data Redaction policy:
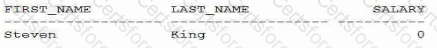
You re-execute the select statement.
What is the result?
A)

B)

C)
D)

E)
Examine this code which executes successfully:
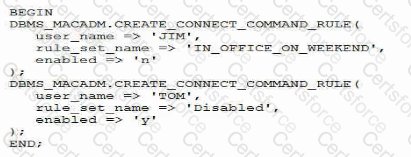
If the IN_OFFICE_ON_WEEKEND rule set returns true for an attempt to connect from Inside the office on weekends, which two are true about the effects of this configuration?
Examine this sqlnet.ora file used by a client application:
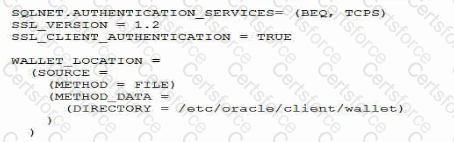
Which three are found in the wallet specified by the directory parameter?
Database Vault realm r protects all tables In the fin schema from DBA access User fin is configured as the owner in realm R.
You must also prevent access to realm r protected tables by user FIN. Which achieves this?