When creating labels using Oracle Label Security, which is required?
To avoid hard coding passwords in scripts, you have elected to create an external password store-Examine this list of steps:
1. Set the external password store wallet location.
ALTER SYSTEM SET EXTERNAL_KEYSTORE_CREDENTIAL_LOCATION = "/•tc/ORACLE/WALLETS/orcl/external_Btore" SCOPE c SPFILE;
2. Log in as a user who has syskm privileges.
3. Create an auto-logln keystore that contains the keystore password including the add secret clause.
ADMINISTER KEY MANAGEMENT ADD SECRET 'password'
FOR CLIENT 'TDE_WALLET'
TO LOCAL AUTO_LOGIH KEYSTORE '/etc/0RACLE/WALLETS/orcl/extemal_store';
4. Restart the database instance as sysdba.
SHUTDOWN IMMEDIATE STARTUP
5. Create an auto-logln keystore that contains the keystore password.
ADMINISTER KEY MANAGEMENT
FOR CLIENT 'TDE_WALLET'
TO LOCAL AUTO_L0GIN KEYSTORE ' /etc/ORACLE/WALLETS/orcl/external_store' ;
6. Set an Encryption Key.
ADMINISTER KEY MANAGEMENT SET ENCRYPTION KEY IDENTIFIED BY keystore_password WITH BACKUP
Identify the minimum number of steps in the correct order that must be performed to create the external password store.
What Is the first step when analyzing security within a database?
Which two statements are true about Database Vault factors?
A policy predicate function Is associated with an enabled Virtual Private Database (VPD) policy for a table.
Which two arguments are passed to the function?
Examine this output:
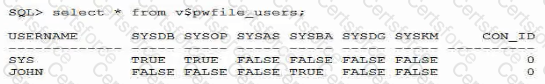
Which three are true?
You must disable OS authentication for database administrative users on a RAC database.
Which option must you use to do this?
You export and Import a table's data using Data Pump connected as a user who Is assigned DBA role with default privileges.
There is a data redaction policy on the table.
Which two statements are true about the redaction policy?
Using Unified Audit, you must determine who performed an pkan backup ot recovery operations on a database.
You are connected as sysdba.
Which statement(s) achieve this?
A)

B)
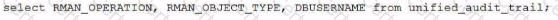
C)
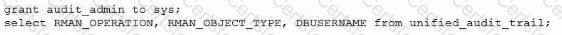
D)
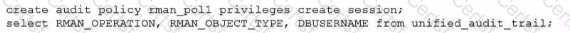
E)

For which two reasons would you define Network ACLs?