You are working with traffic from applications with pinned certificates. In this scenario, which statement is correct?
You have applied a DLP Profile to block all Personally Identifiable Information data uploads to Microsoft 365 OneDrive. DLP Alerts are not displayed and no OneDrive-related activities are displayed in the Skope IT App Events table.
In this scenario, what are two possible reasons for this issue? (Choose two.)
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?
You want to enable Netskope to gain visibility into your users' cloud application activities in an inline mode.
In this scenario, which two deployment methods would match your inline use case? (Choose two.)
The Netskope deployment for your organization is deployed in CASB-only mode. You want to view dropbox.com traffic but do not see it when using SkopeIT.
In this scenario, what are two reasons for this problem? (Choose two.)
You are working with a large retail chain and have concerns about their customer data. You want to protect customer credit card data so that it is never exposed in transit or at rest. In this scenario, which regulatory compliance standard should be used to govern this data?
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?
Which three technologies describe the primary cloud service models as defined by the National Institute of Standards and Technology (NIST)? (Choose three.)
Exhibit
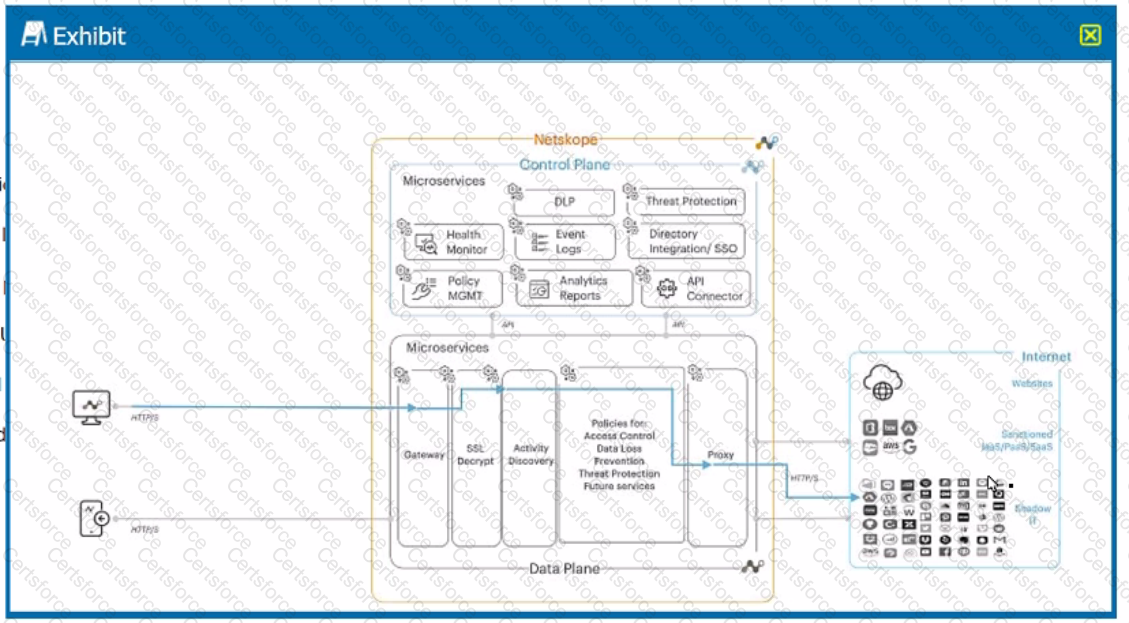
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)